OneLogin
In this document you are going to set up IDmelon as an external IdP to the OneLogin.
Login to OneLogin administration panel
- Login to OneLogin.
- Open OneLogin dashboard.
- On the right side of navbar click onAdministration
Add Identity Provider
- Tab then click on Trusted idps
- Click on New Trust
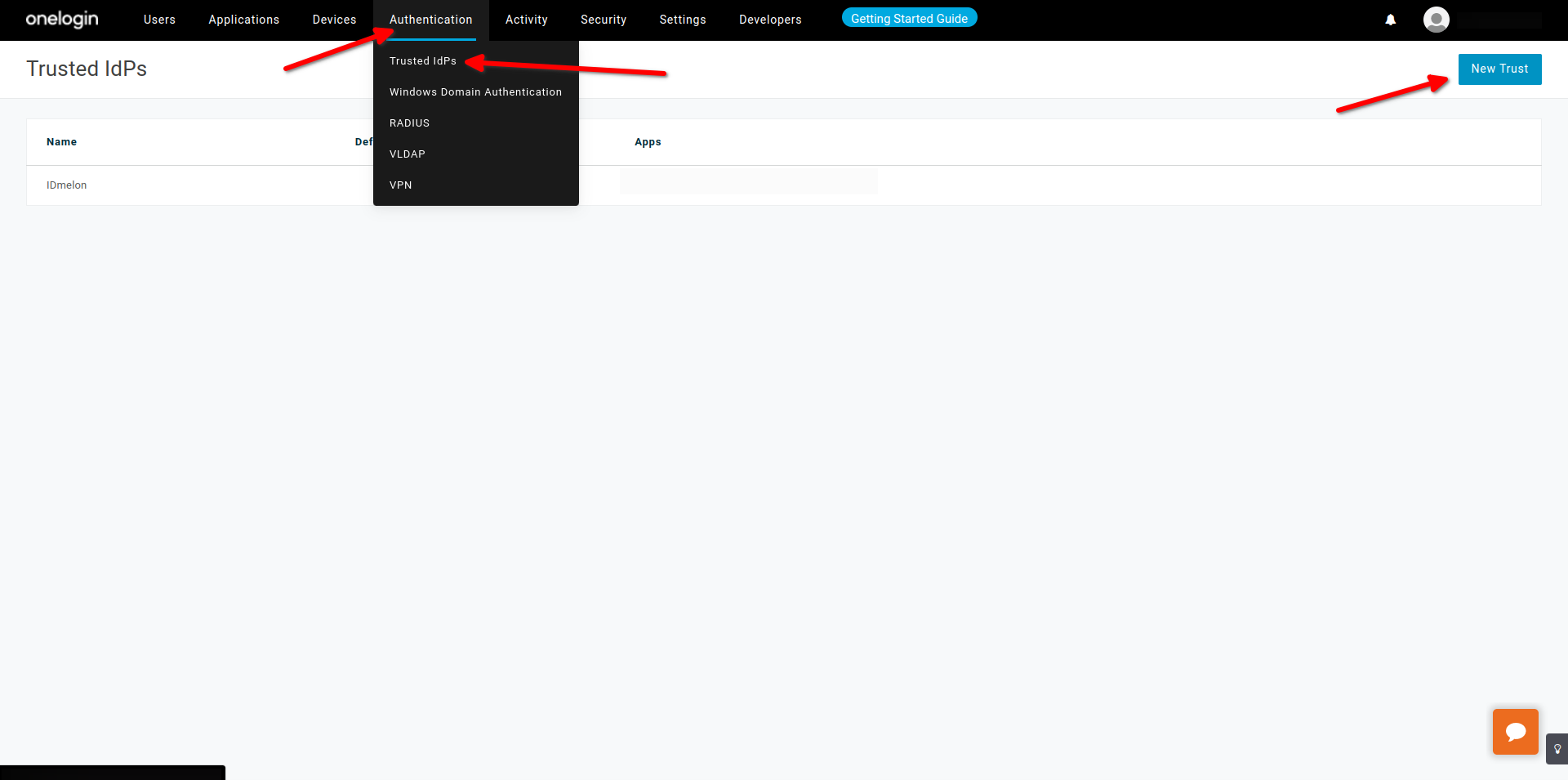
- Choose a custom name at the left side of page
- Enable Trusted IDP, for this action certificate validation is necessary
- Enable Show in Login panel, Choose Custom logo
- IDmelon Logo Domain :
Get all values for
{..}from your IDmelon panel. If you are currently login here, you will see the replaced values instead.
- Issuer : Show in Login panel, idp_issuer_uri
- Email Domains : The Email Domains field is used to automatically invoke this Trusted IdP when a user enters their email address at login time - if the email address is unrecognized, but belongs to one of the domains listed, then this TIdP will be invoked via an authentication request (SAML, OIDC or OAuth as appropriate), Example = idmelon.com
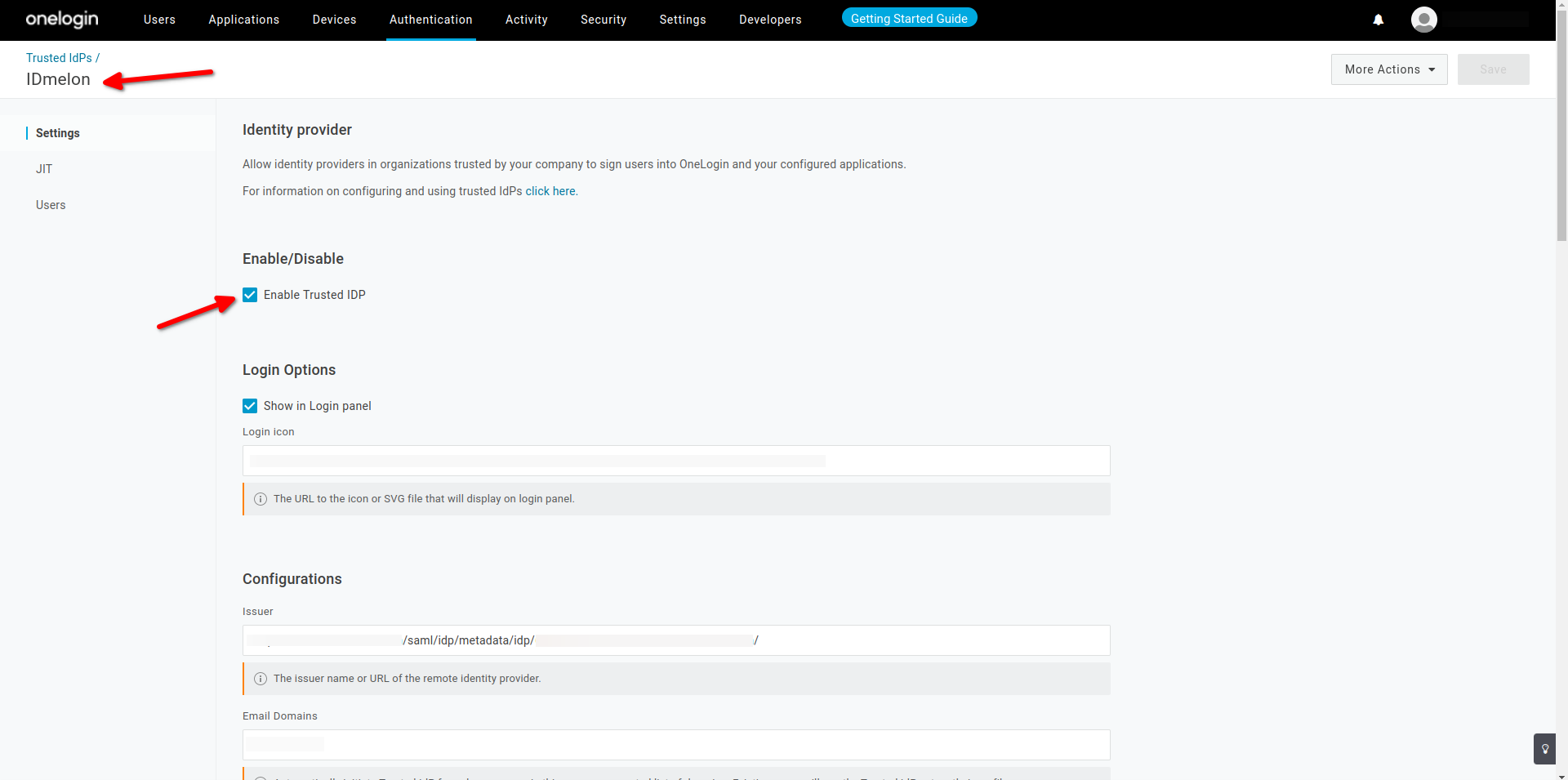
- To enable Standard mode, check Sign users into OneLogin. This allows inbound identities from the Identity Provider to be matched to local user accounts within the tenant, via responses to the /access/idp endpoint.
- To send the user identity within the authentication request sent to the Trusted Identity Provider, check Send Subject Name ID or Login Hint in Auth Request: if the Trusted IdP is configured to use SAML, then the authentication request is sent as a Subject NameID parameter whilst if OIDC or OAuth is used, the same information is sent as a query string parameter called login\_hint. This feature is to provide an improved user experience by avoiding the need for the user to provide an identifier to both OneLogin and the Trusted IdP.
- Sign users into OneLogin
- Send Subject Name ID or Login Hint in Auth Request
- SAML - hard-coded to extract the SAML Subject NameID. It can’t be changed.
- User Attribute Mapping : Email
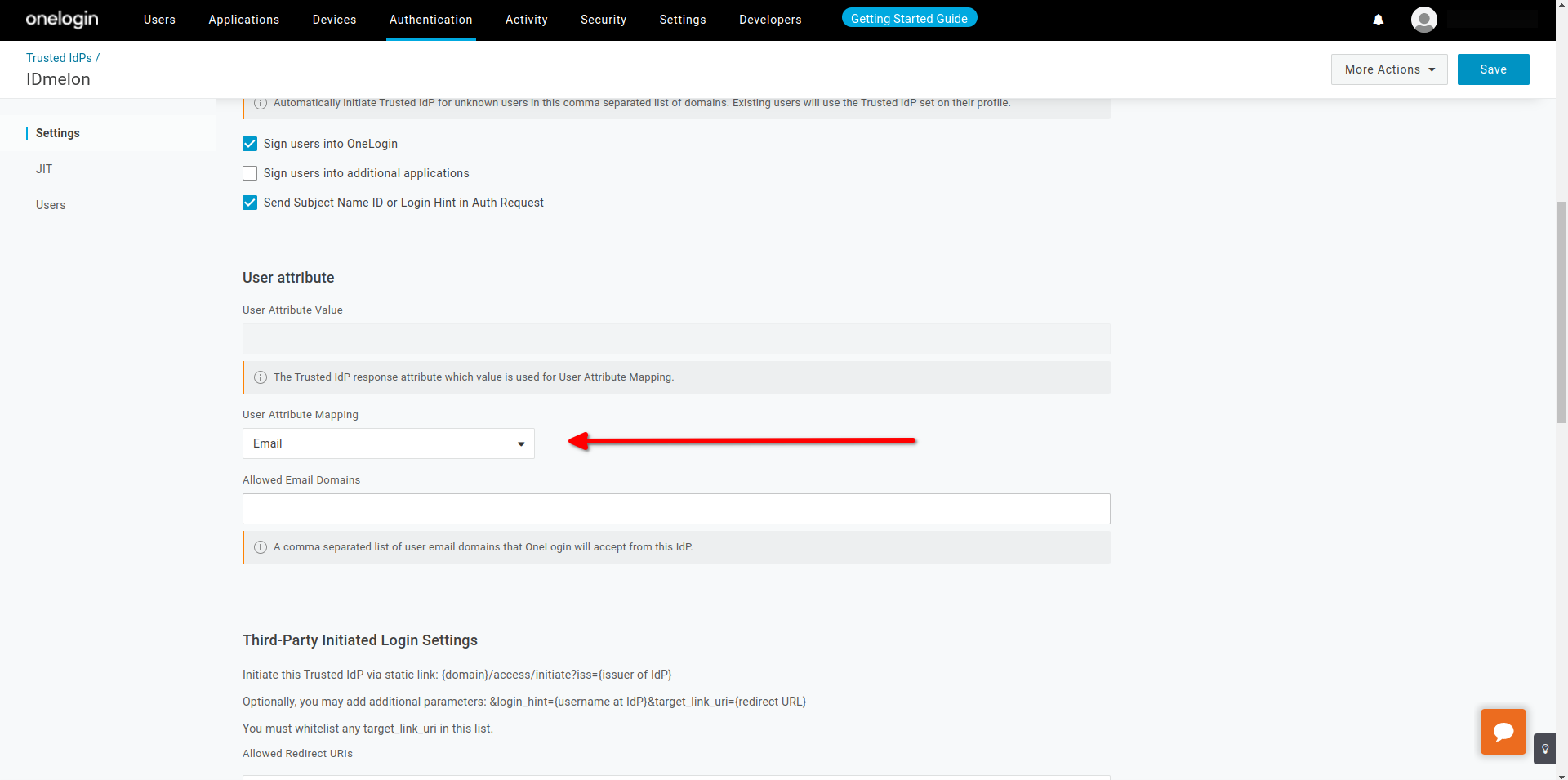
Get all values for
{..}from your IDmelon panel. If you are currently login here, you will see the replaced values instead.
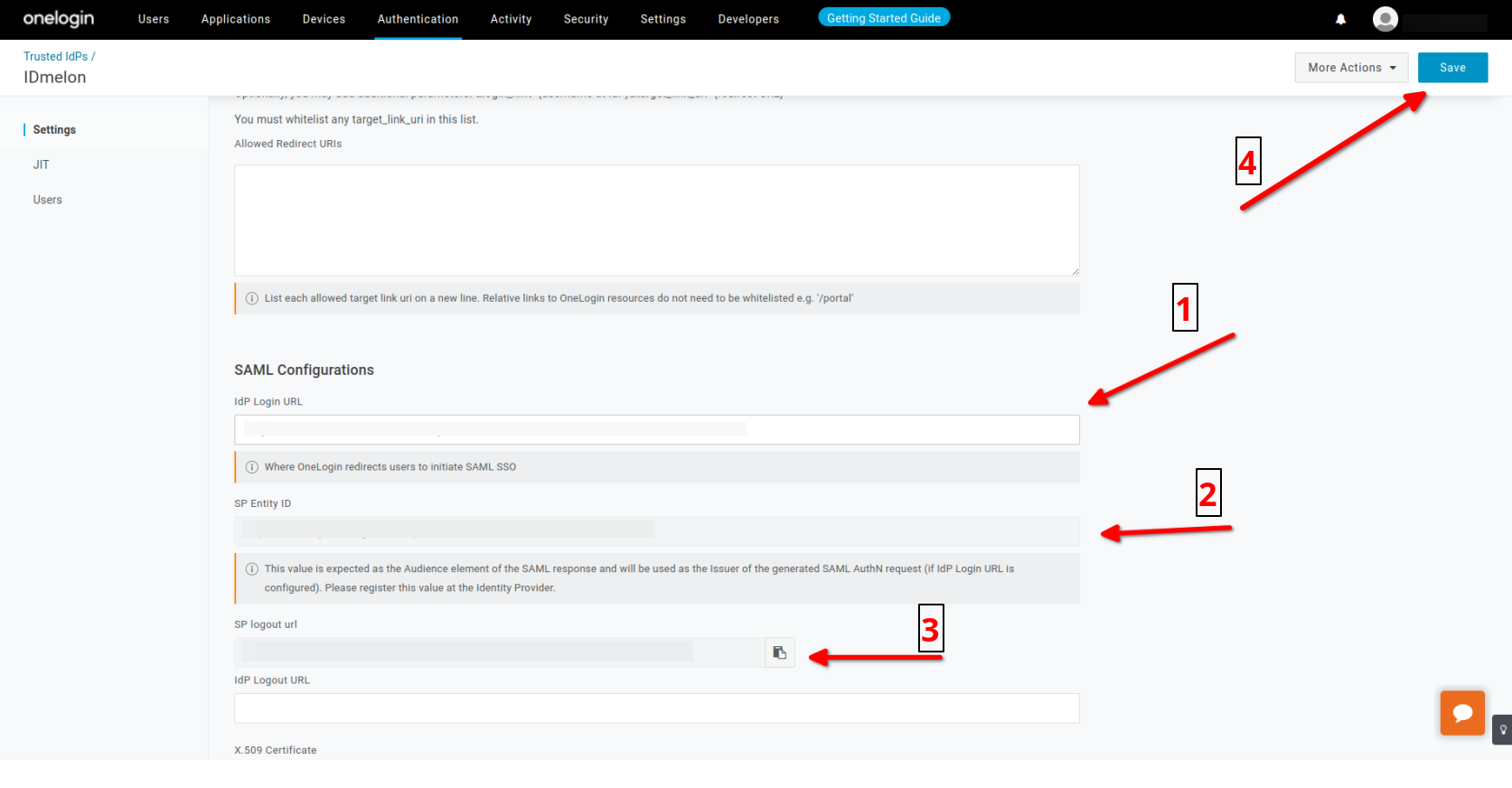
- IdP Login URL : idp_single_sign_on_url
- IdP Logout URL : idp_single_sign_on_url
- IdP Issuer URI idp_issuer_uri
Note : please save the configuration then scroll it to continue with certificate part.
IDmelon SAML configuration
You should copy values of below fields from the Okta panel to the IDmelon Panel:
- entity id: Copy SP Entity ID
- single log out: Copy SP logout url
- Assertion Consumer Service URL :
https://{your custom subdomain}.onelogin.com/access/idp
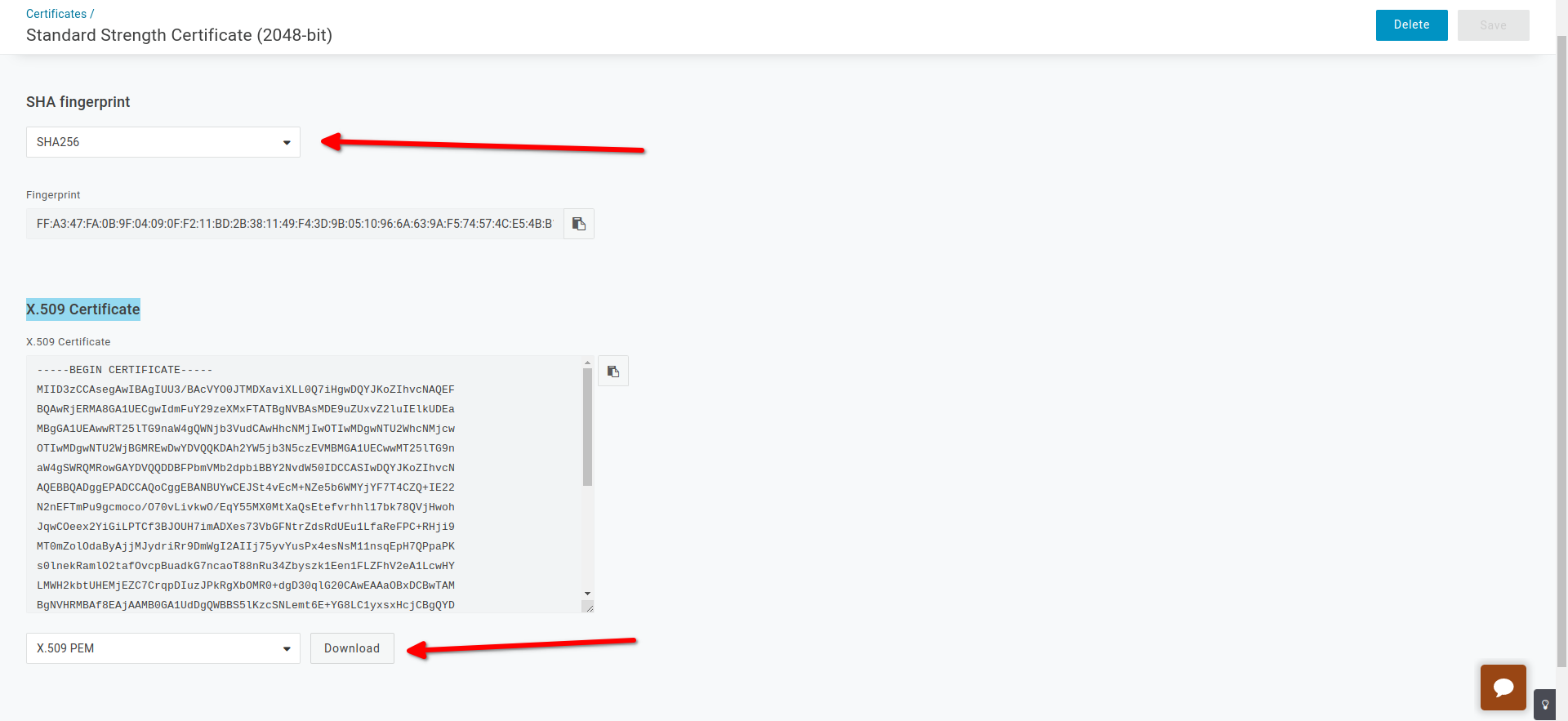
- Choose : X.509 Certificate = Standard Strength Certificate (2048-bit)
- Choose : X.509 Certificate = Standard Strength Certificate (2048-bit)
- Click on View Details
- Choose : SHA256
- Download : X.509 Certificate
- Click on Save
- Trusted IdP Certificate :
idp_certificate_download_url - JIT : Enable, Set User TIDP after user creation
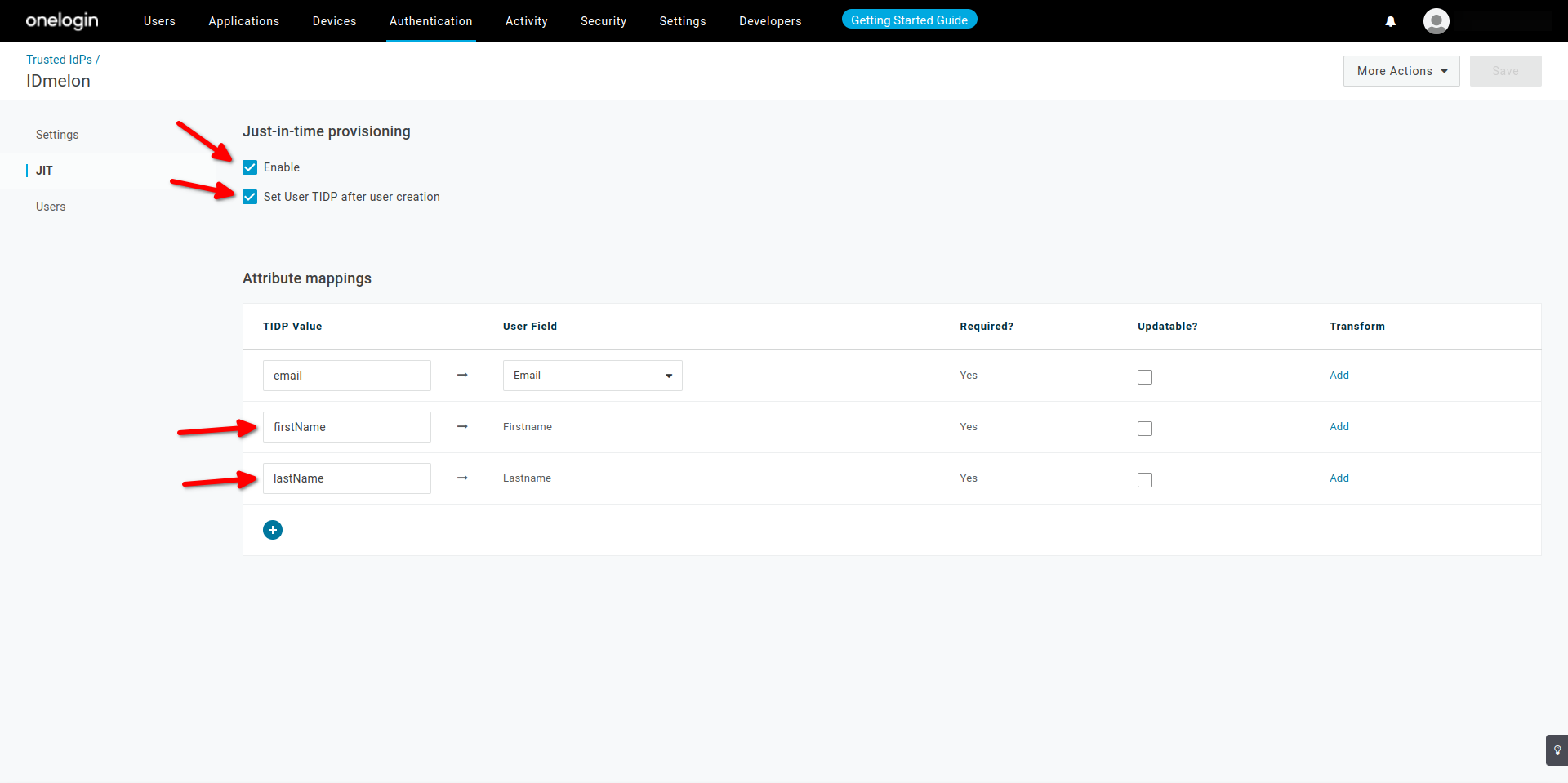
- Enable
- Set User TIDP after user creation
- Click on Save.
Enable SSO
- Click on More Actions then click on Set as default Trusted Idp.
- this option will activate sso for all users..
- OR Enable sso for special users.
- Click on specialuser then Click on Authentication.
- Choose Custom Trusted IDP.
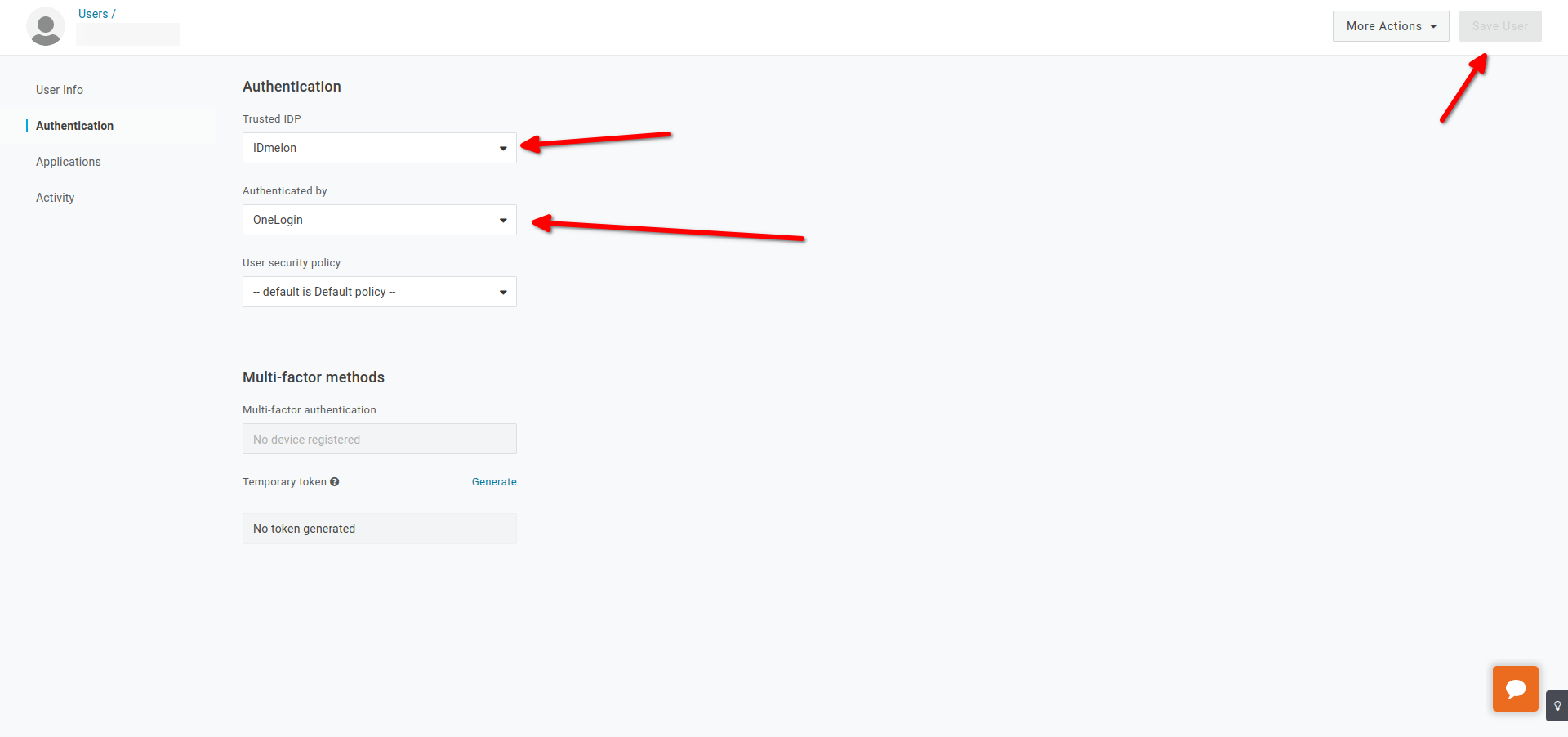
- Click on Save.
API Token
GET API Token for user provisioning in OneLogin
- Click on Developers then API Credentials.
- Click on New Credential .
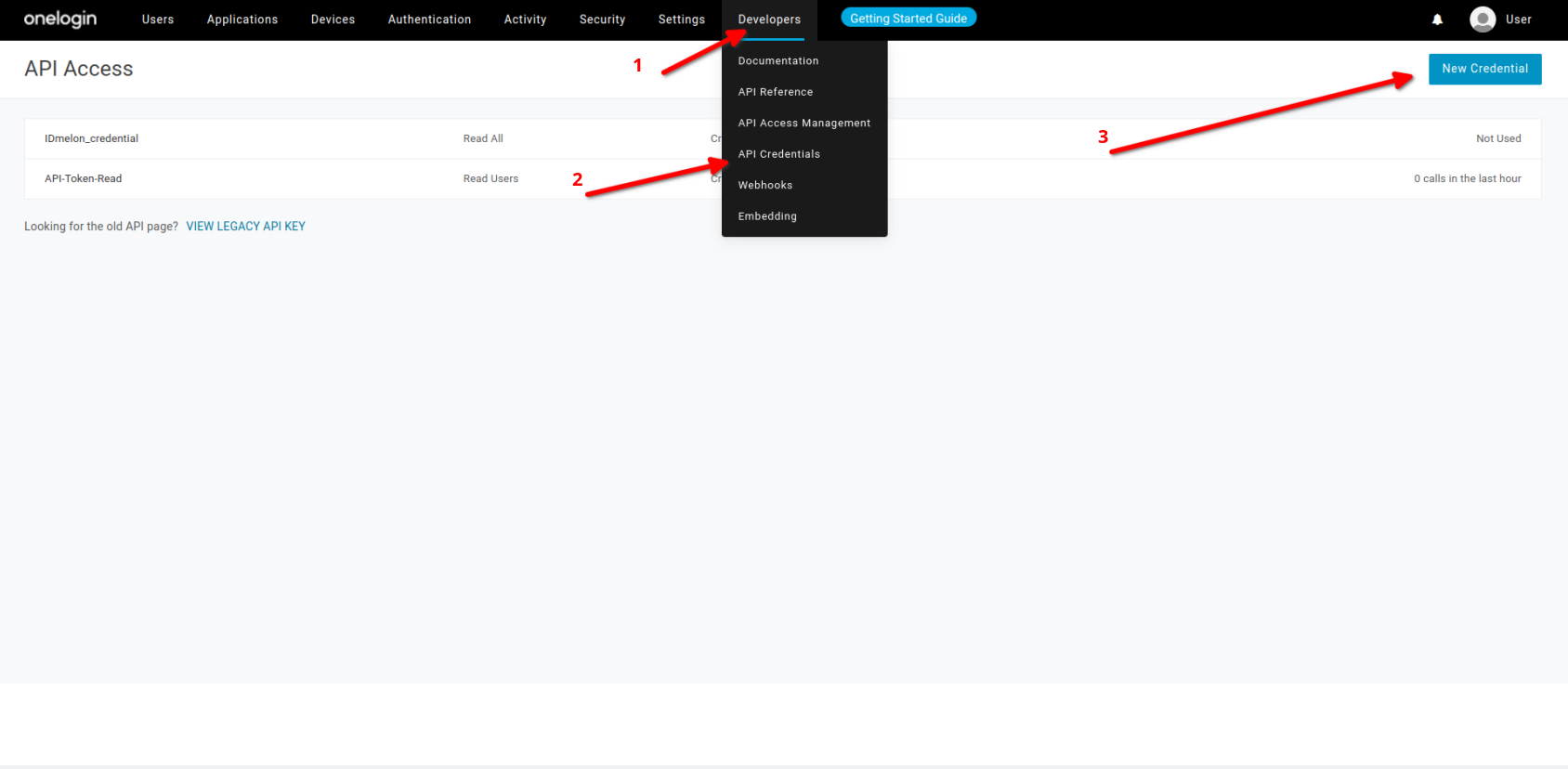
- Choose Custom Name.
- Click on Manage all.
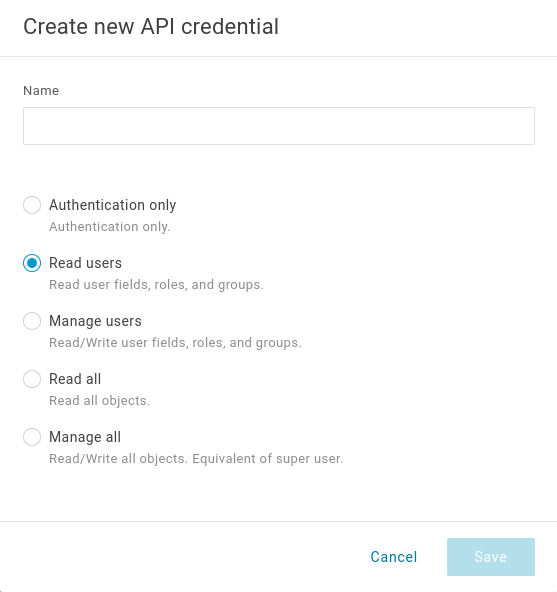
- Save.
Custom name API Copy Client ID
- Copy Client Secret.
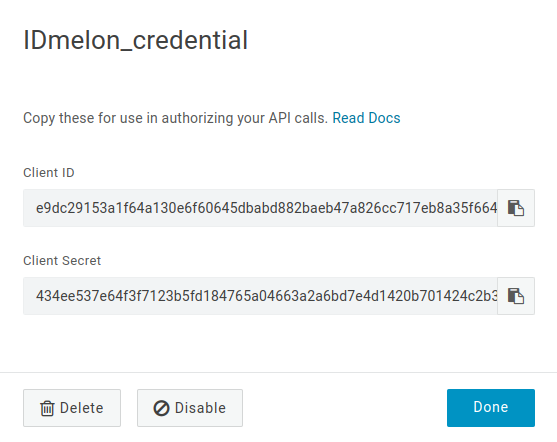
- Done.