Office
In this document you are going to set up IDmelon as an external IdP to the Office.
Execute these commands in the Windows Power Shell
$cred = Get-Credential
Connect-MsolService -Credential $cred
Get-MsolDomain
Get all values for
{..}from your IDmelon panel. If you are currently login here, you will see the replaced values instead.
$dom = domain
$uri = idp_issuer_uri
$url = idp_single_sign_on_ur
$logouturl = idp_single_sign_on_url
$cert = idp_certificate_download_url
Set-MsolDomainAuthentication -DomainName $dom -FederationBrandName $dom -Authentication Federated
-PassiveLogOnUri $url -SigningCertificate $cert -IssuerUri $uri -LogOffUri $logouturl
-PreferredAuthenticationProtocol SAMLP
Check your SAML configuration
the result is :
$dom = domain
Get-MSolDomainFederationSettings -DomainName $dom | Format-List *
You need to Set ImmutableID for your current user
Example of users.csv file:
UserPrincipalName
[email protected];
[email protected];
Load CSV
$csvFile = Import-Csv C:\\idmelon\\users.csv -Delimiter ";"
Create arrays for skipped and failed users
$SkippedUsers = @()
$FailedUsers = @()
Loop through CSV records
foreach ($item in $csvFile) {
$upn = $item.UserPrincipalName
$UserPrincipalName = (Get-MsolUser -UserPrincipalName $upn | select UserPrincipalName).UserPrincipalName
$objectID = (Get-MsolUser -UserPrincipalName $upn | select ObjectId).ObjectId.Guid
if ($UserPrincipalName) {
try{
Set-MSOLuser -UserPrincipalName $UserPrincipalName -ImmutableID $objectID
} catch {
$FailedUsers += $upn
Write-Warning "$upn user found, but FAILED to update."
}
}
else {
Write-Warning "$upn not found, skipped"
$SkippedUsers += $upn
}
}
foo()
Show result
Get-MsolUser -all | Select-Object UserprincipalName,objectID,ImmutableID
Passwordless
- Open Azure directory admin.
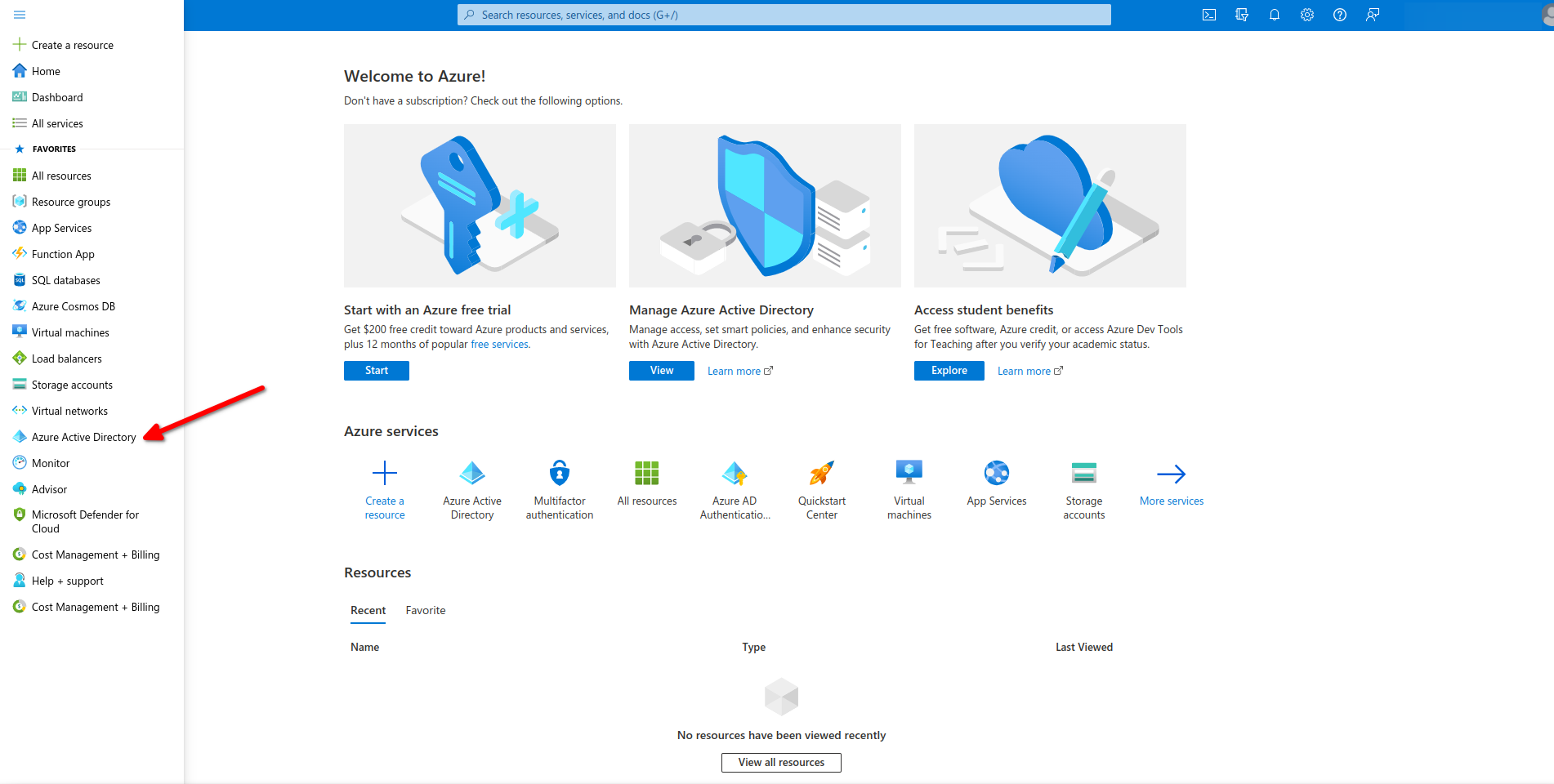
- Click on users.
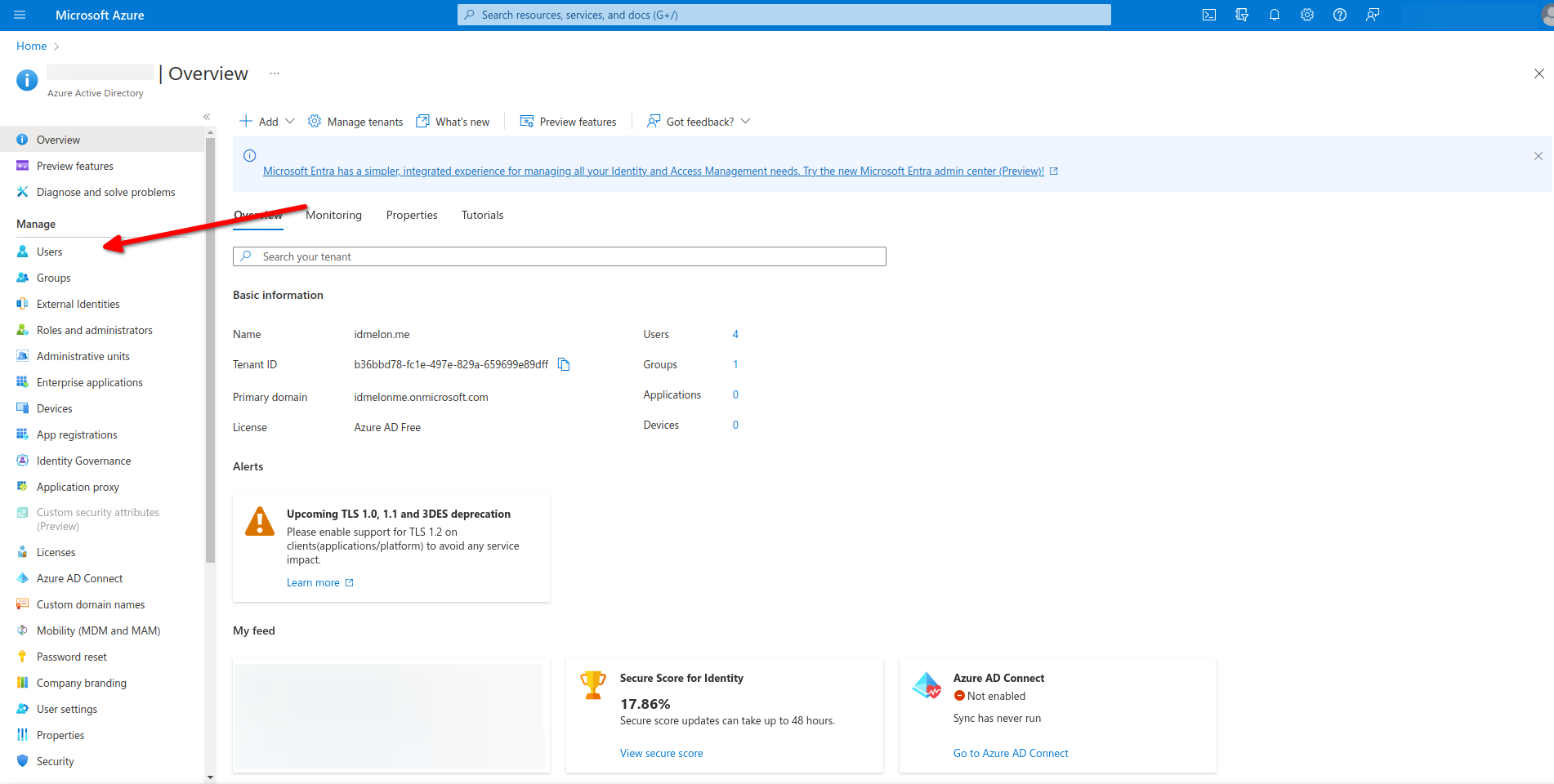
Choose a user.
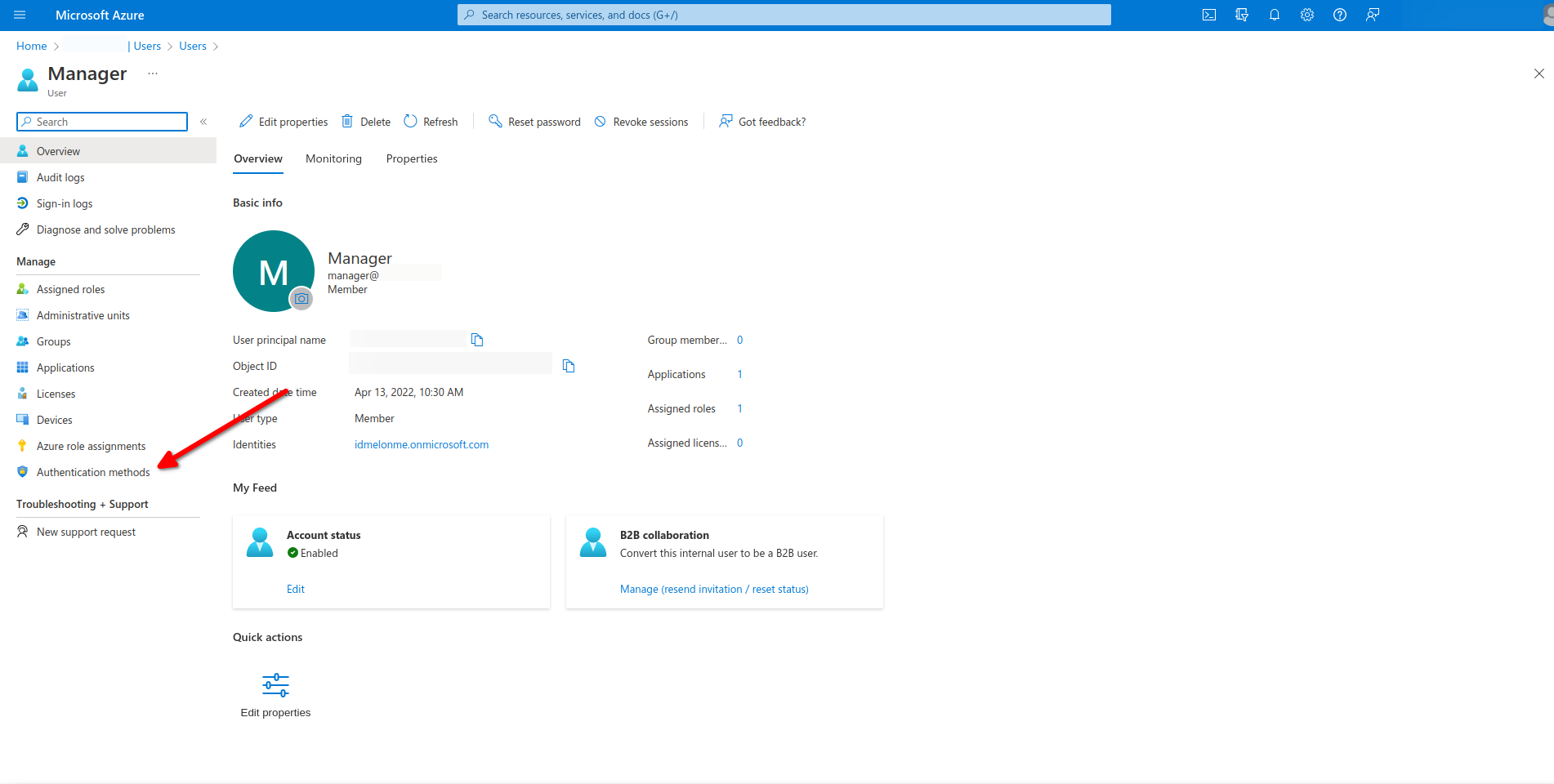
Click on Authentication methods.
Delete Authentication method option.
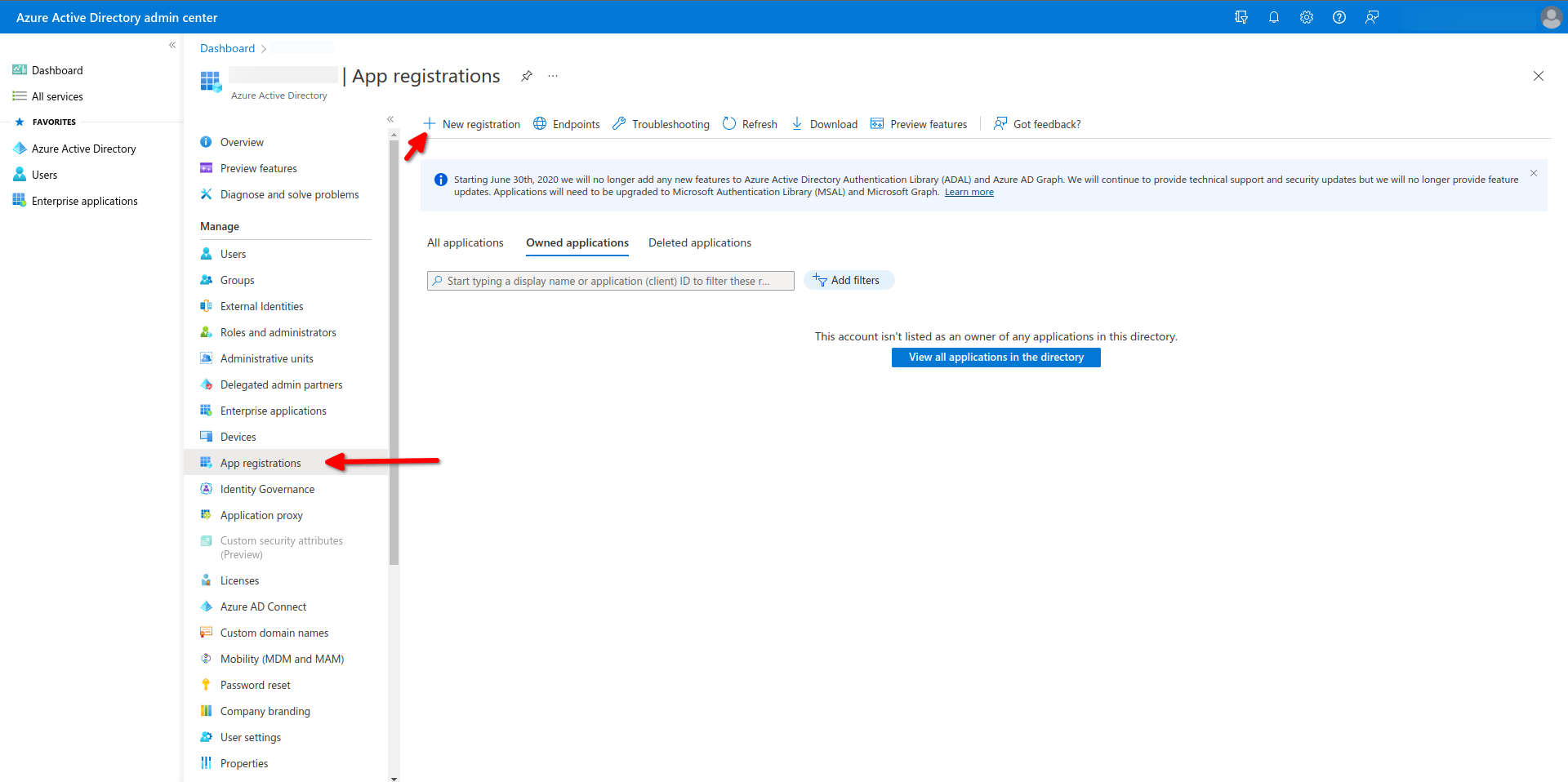
API Token
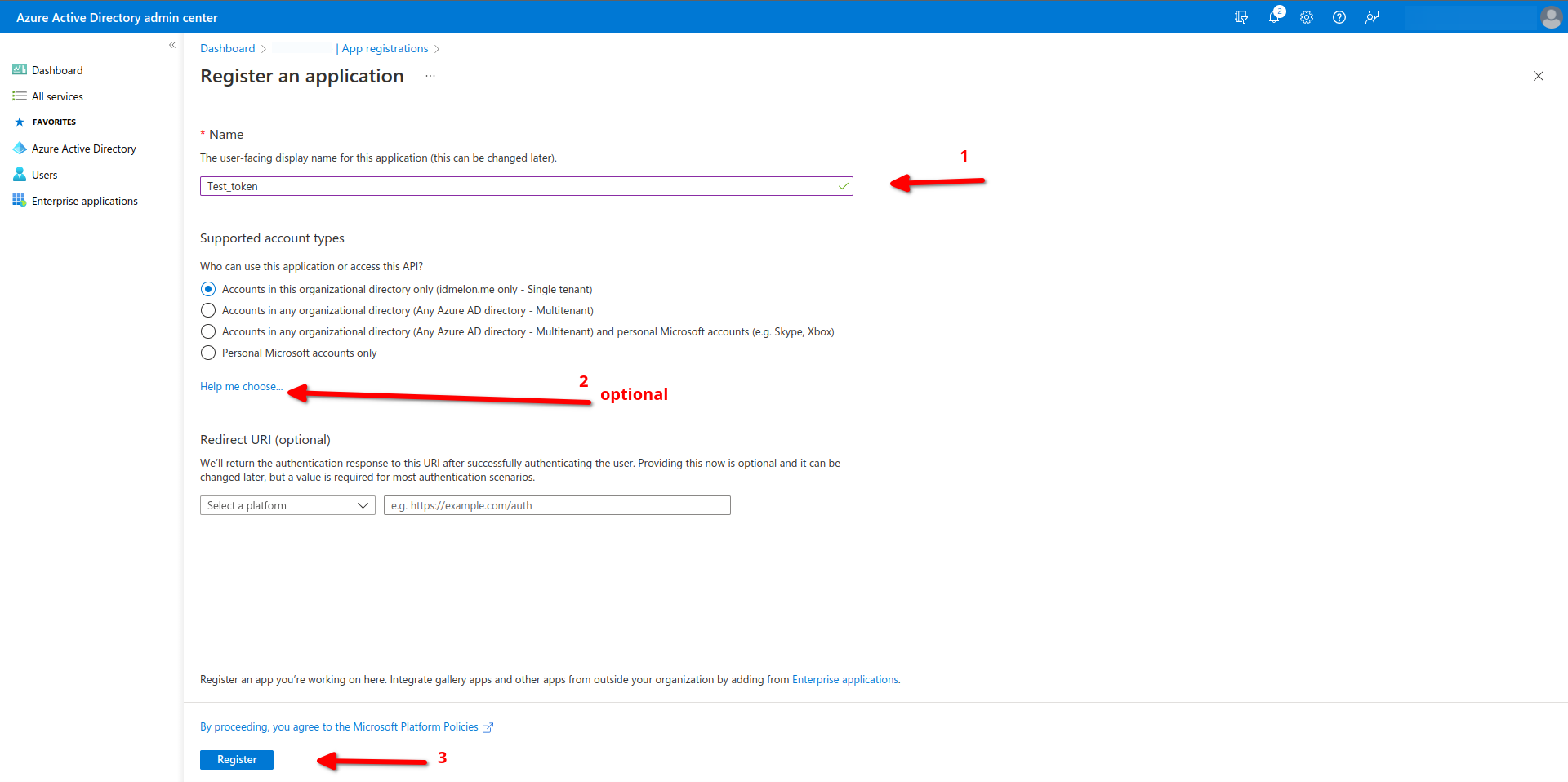
From the side menu, navigate to the App registrations menu and click New registrations.
Enter the desired name for your Application.
Then from
Supported account typesselect who can use your API.- Tip : for more information of the choices please select Help me Choose….
Click Register.
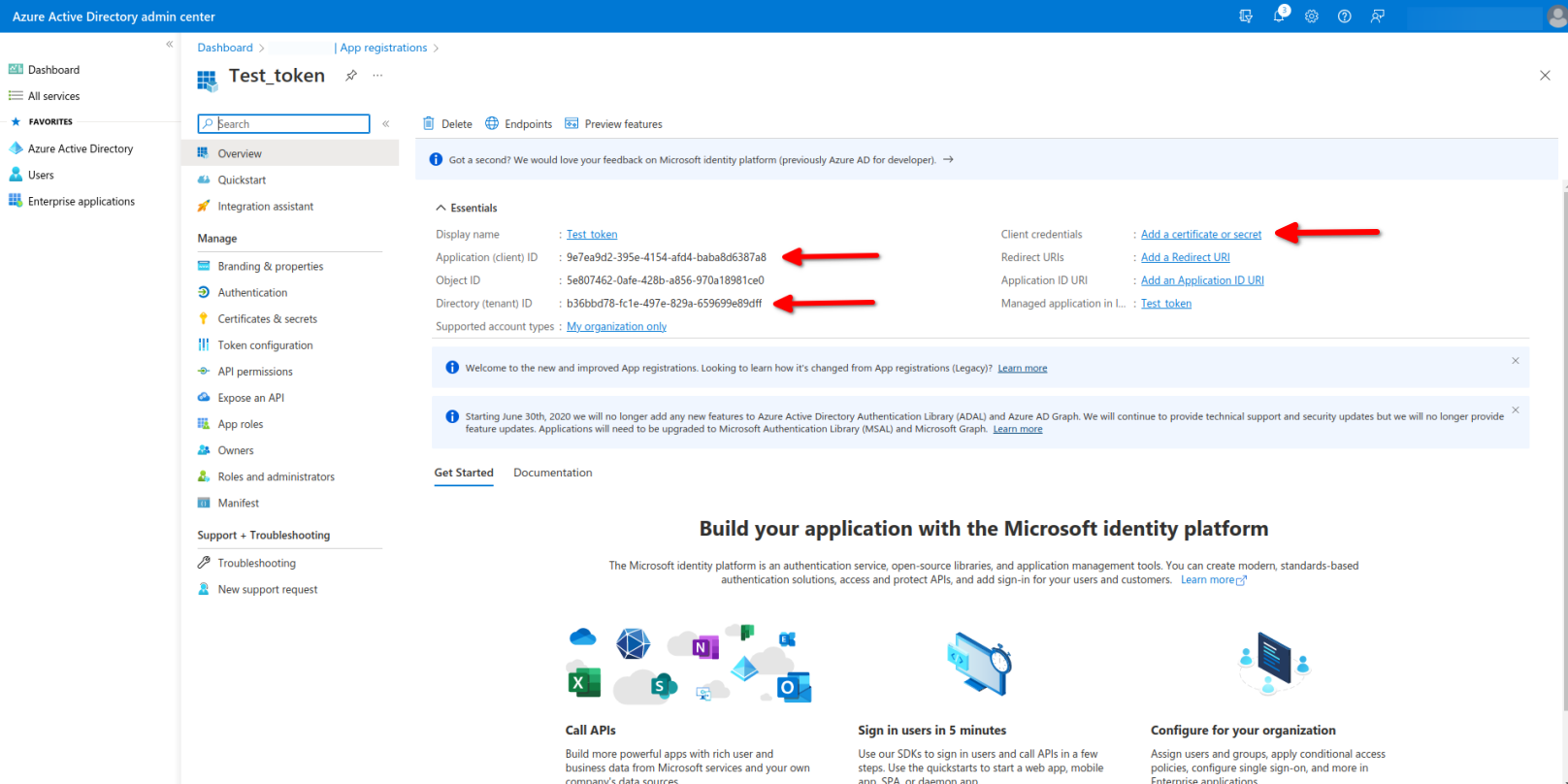
Then you can see your API information, which you have Copy and send these informations to idmelon.
Copy Application (client) ID.
Copy Directory (tenant) ID.
Then please for accessing to Client Secret click Add a certificate or secret in Client credentials field.
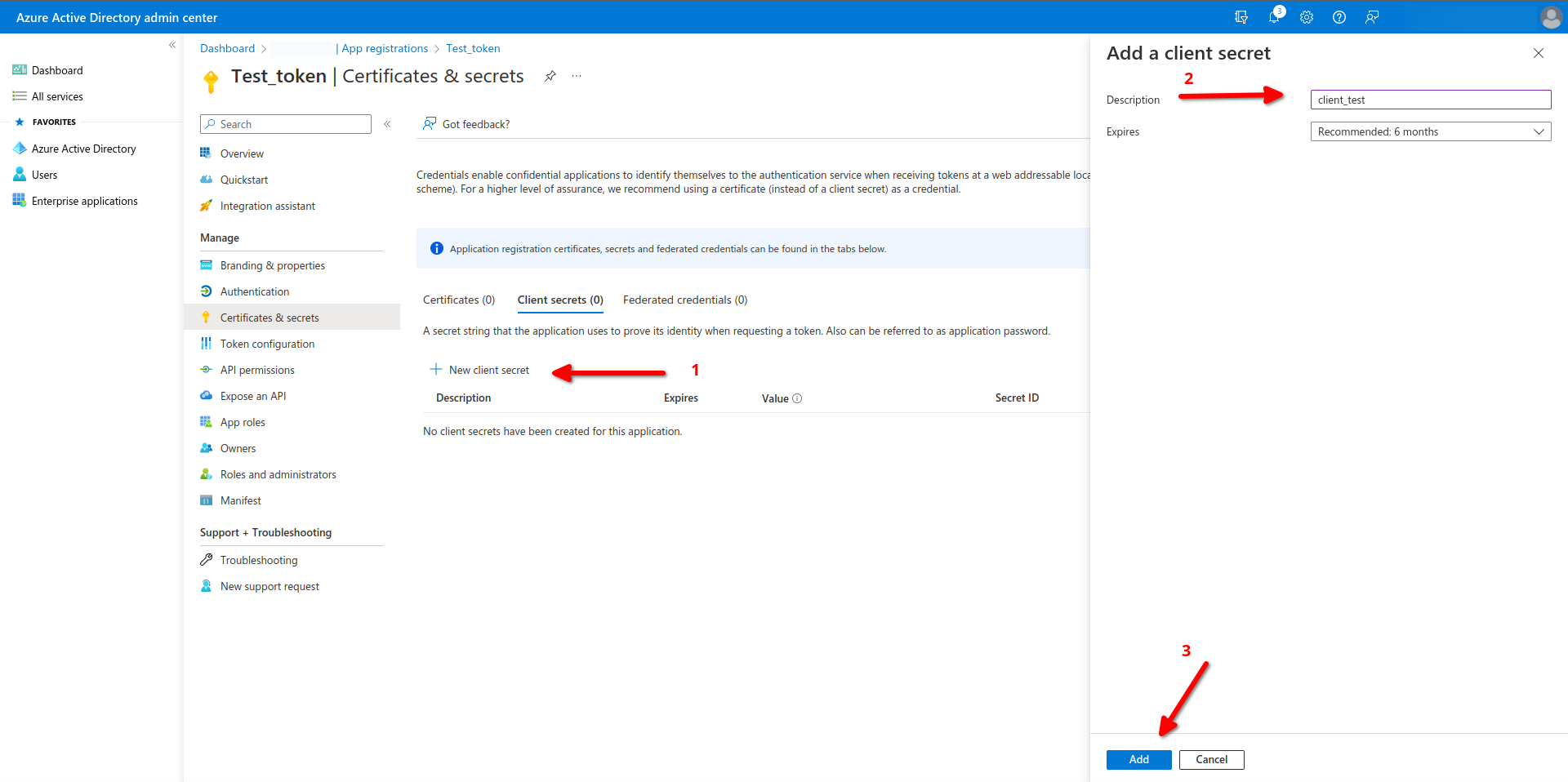
From Certificate & secrets panel please click on New client secret :
Enter the desired description for your client secret.
Click
Add.
Finally, you can Copy your client secret from Client credentials field.

Please send these information to IDmelon, in order to get your users from office panel.