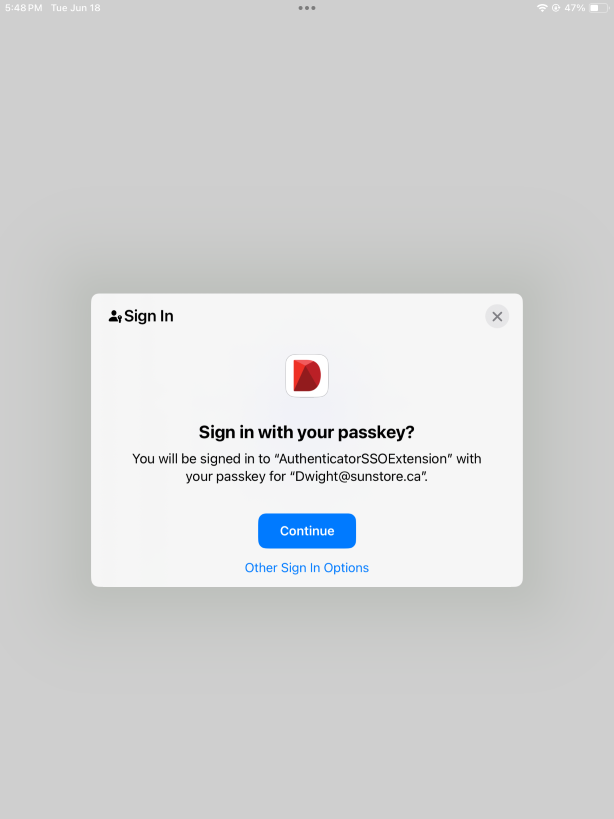
Shared iOS/iPadOS Devices
Shared mobile devices are widely used across many industries, including manufacturing and retail. IDmelon Authenticator can be configured in shared device mode, enabling users to use their badge or biometric factors to load passkeys or passwords into the device instantly. This allows users to access multiple applications with auto-login. The session time-to-live can be configured to support various shift change use cases with auto logout.
IDmelon Authenticator Shared Configuration Mode Features
- Passkeys Autofill (or passwords for legacy devices)
- MSAL Configuration to streamline access to Microsoft apps
- SSO Integration
- JAMF Configuration (can be configured with Jamf Setup and Jamf Reset app)
Shared Device Mode Configuration Using Jamf
Jamf is a trusted solution for managing iPads in various organizations, including businesses, schools, and hospitals. With over 70,000 customers, Jamf provides robust iPad management capabilities.
Prerequisites
- To use the shared iPad feature, the OS version of iPads must be 17 or later.
- IDmelon Authenticator app must be added to Jamf Pro. In case you are having issues with that, contact Jamf Support.
How to Configure
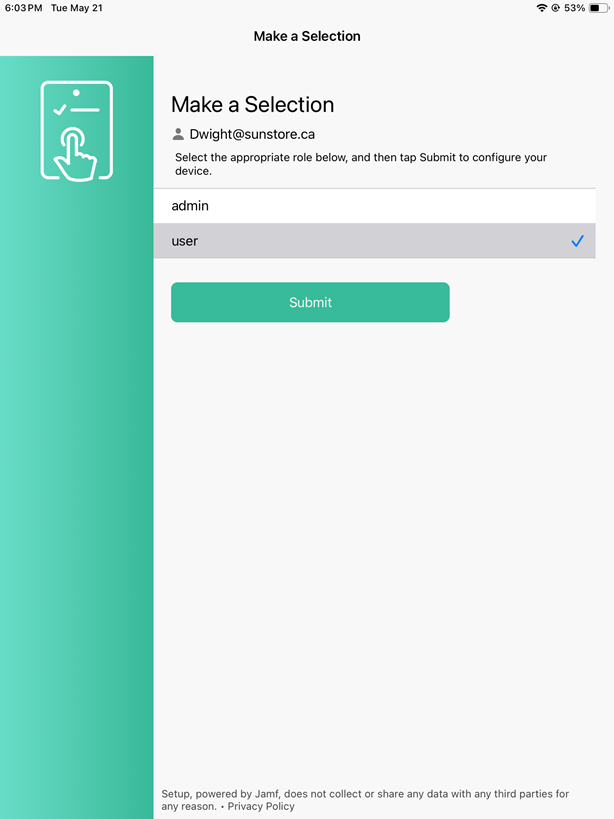
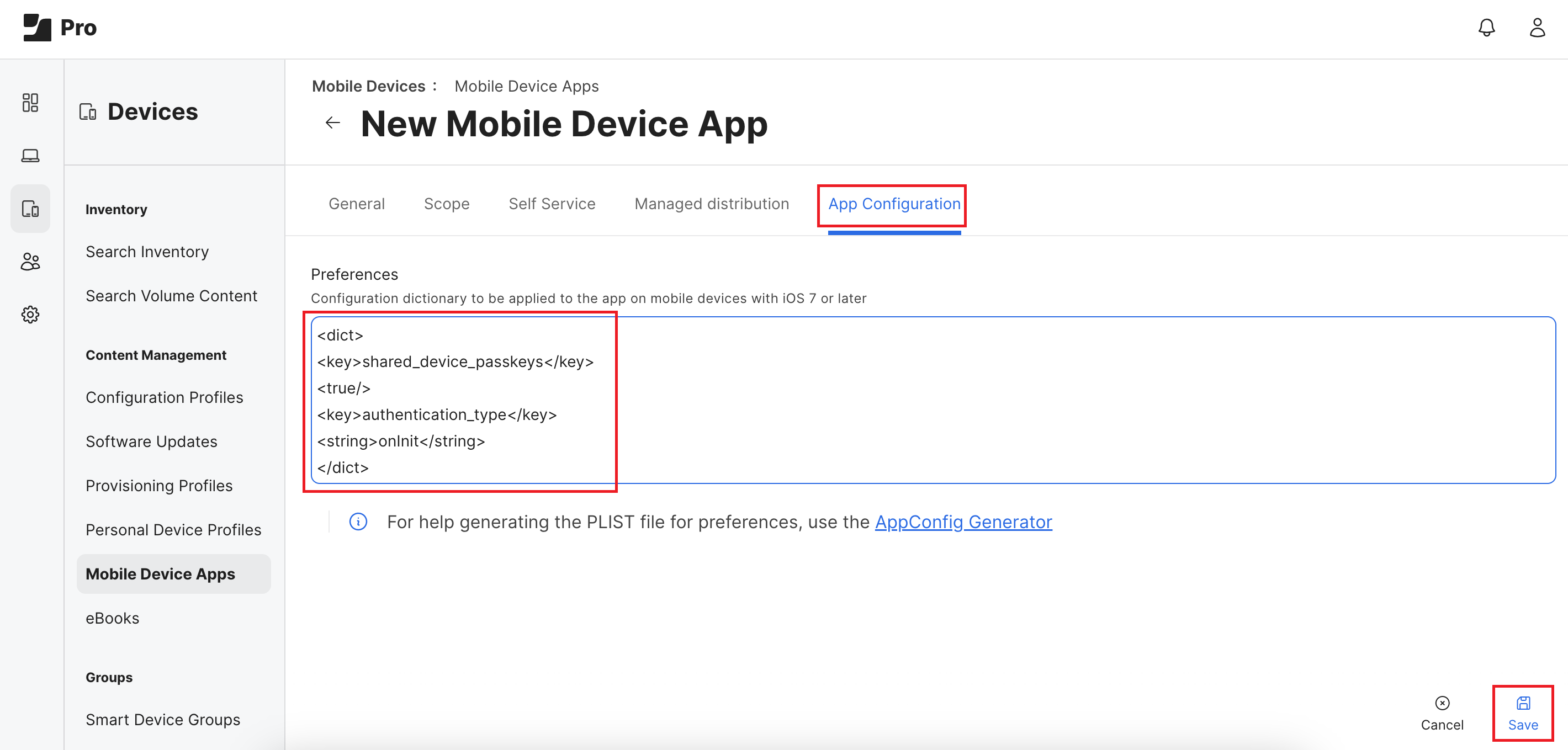
- Configure General, Scope and Self-Service according to your organization’s policies.
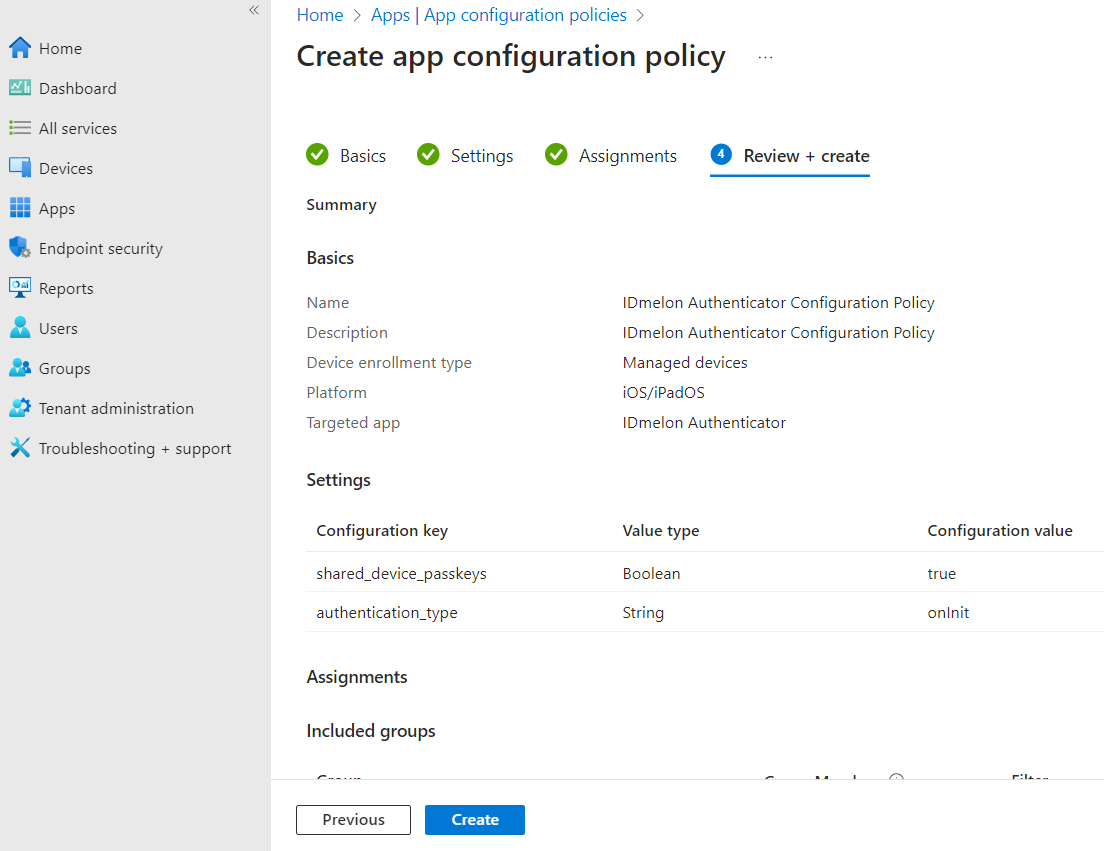
- Select the App Configuration tab from the menu, enter the following configuration as shown in the image below, and then click the Save button.
<dict>
<key>shared_device_passkeys</key>
<true/>
<key>authentication_type</key>
<string>onInit</string>
<key>device_id</key>
<string>$UDID</string>
<key>api_key</key>
<string>[API_KEY]</string>
</dict>
One-Time Use Passkeys:
Add the following key to the above configurations to automatically log the user out after their first login with the passkey.
<key>one_time_use_passkeys</key>
<true/>
Dedicated Deployments Base API URL:
If you are using dedicated deployment, such as on-premises, add the following key-value to the configurations.
<key>base_api_url</key>
<string>https://example.com/api/url</string>
Self Service URL:
By adding the self-service URL (available in the IDmelon Admin Panel > Security Keys > Workflows > Self-Service Actions) to the configurations, users will be redirected to the enrollment page if their card is not yet registered.
<key>self_service_url</key>
<string>https://panel.idmelon.com/self-service/{UID}</string>
Auto Logout:
By adding this configuration, users will be automatically logged out of the app after a specified time or after the first use of the passkey.
Allowed values: one-time use, 5m, 60m, 2h, 4h, 6h, 8h
<key>auto_logout</key>
<string>2h</string>
Generate a New API Key:
The API Key is required to activate IDmellon Authenticator automatically when it is run for the first time. Therefore, there would be no need for manual activation to connect to the organization.
To generate a new API Key, take the following steps:
- Sign in to the IDmelon Admin Panel.
- Navigate to Workspace > Settings > API Key Management.
- Select Create.
- Set a name.
- Set the type to Shared Mobile.
- Copy and replace the generated key with the API_KEY value in the app configuration, which can be found in the previous section How to configure.
Note: The value of the authentication_type depends on the Card Verification Method that your organization’s admins have set in the IDmelon admin panel.
Allowed values for authentication_type:
- onInit: User is required to enter PIN once only after tapping the card on a reader.
- onUse: User is required to enter PIN for each login.
- none: The login process is done without entering any PIN (PINless mode).
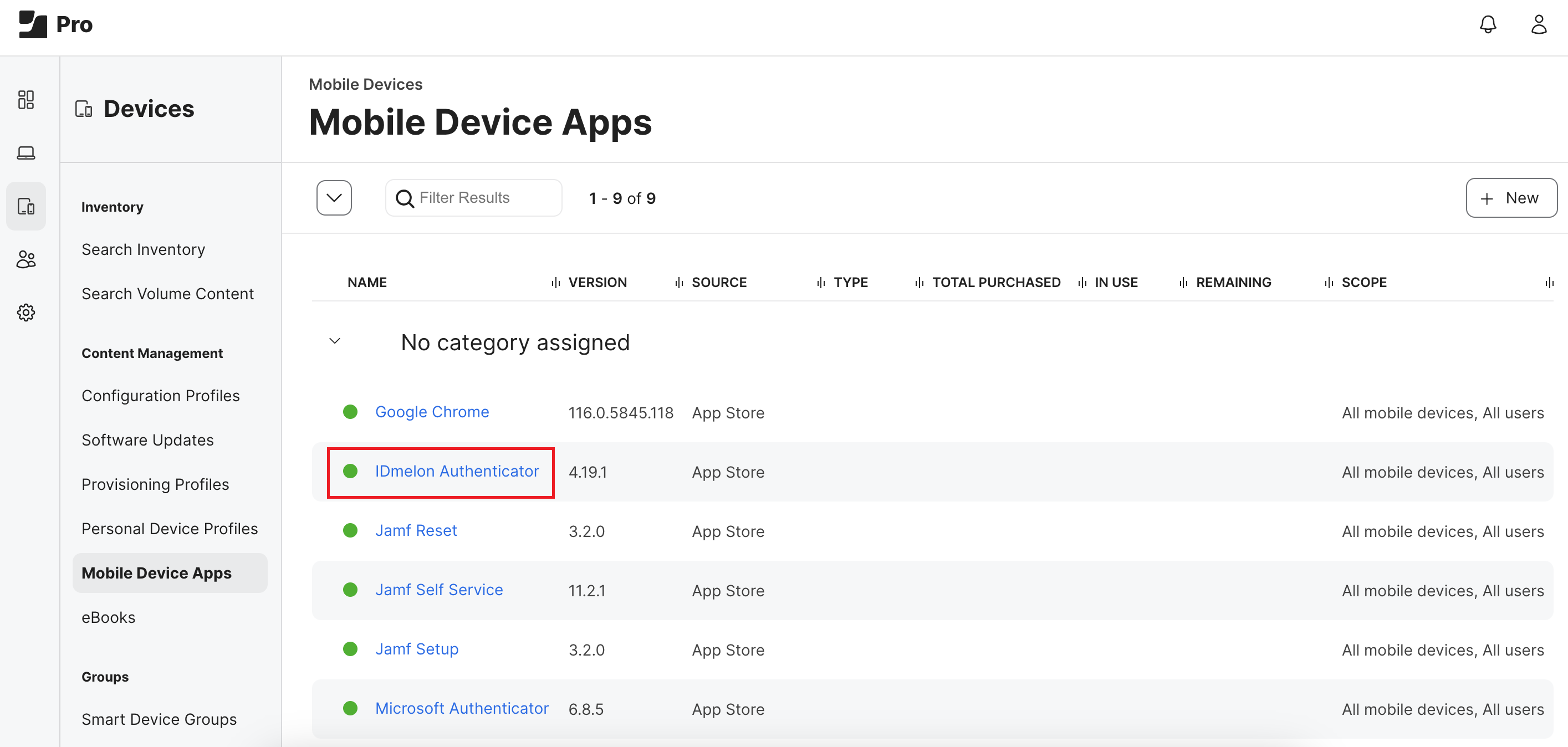
 Finally, you should see the IDmelon Authenticator app in the Mobile Device Apps.
Finally, you should see the IDmelon Authenticator app in the Mobile Device Apps.
Connect to the Organization
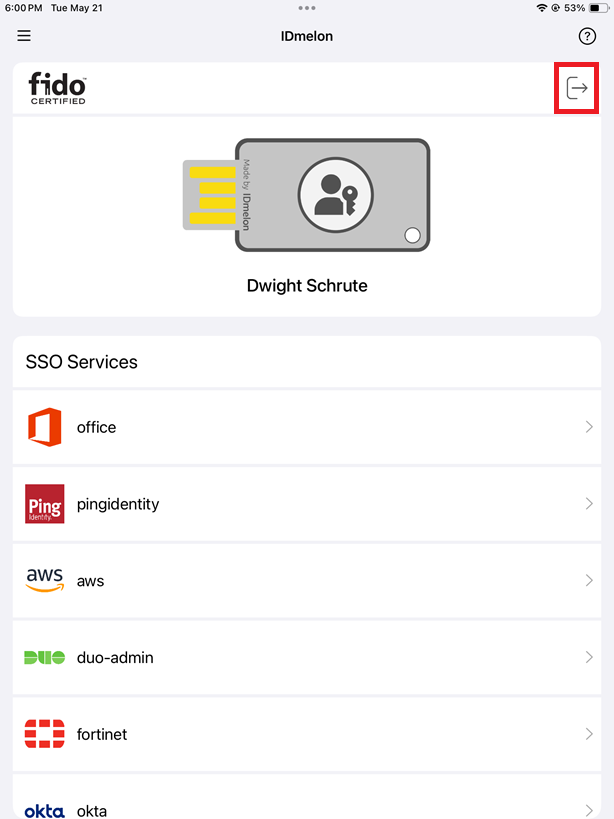
After adding the IDmelon Authenticator to the Jamf Pro panel, the application will be available on iPads as shown in the image below (or it can be installed through Self Service app).
Once the IDmelon Authenticator app opens, the activation process will be completed automatically.
End User Experience
The login steps are as follows: at the beginning of the shift, an employee will first log in with their card, and at the end of the shift, by exiting the application, everything will be ready for the next person.
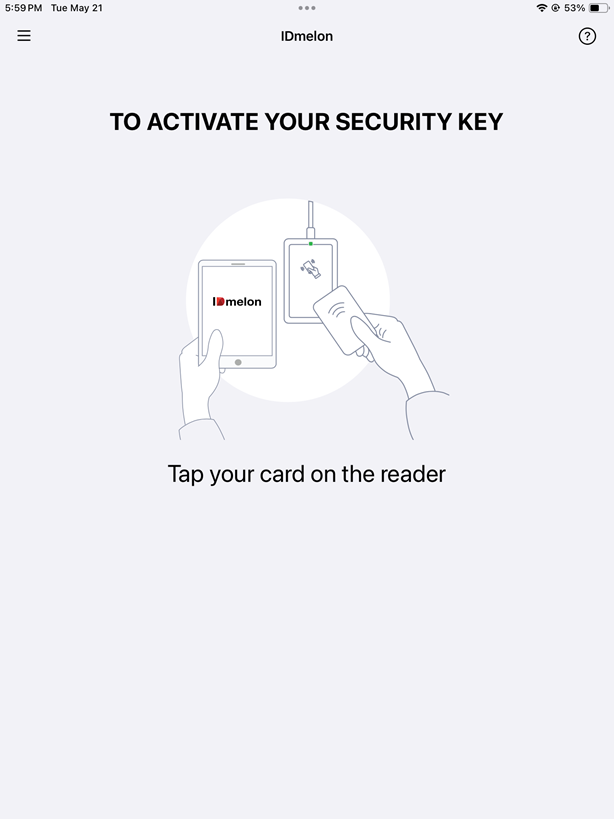
- Open the IDmelon Authenticator.
- Get close to the reader and tap your card on it.
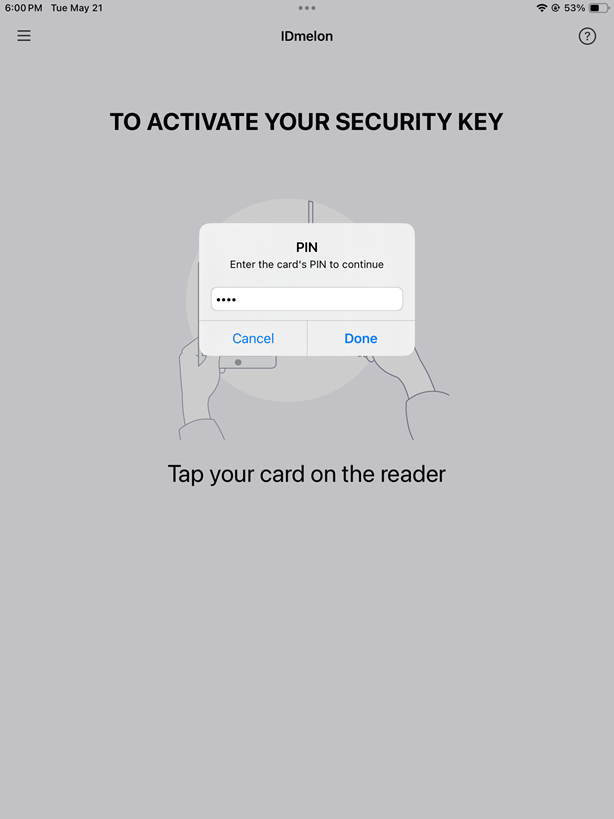
- According to the Card Verification Method set in the IDmelon admin panel, if PIN is required, enter it. Otherwise, go to the next step.
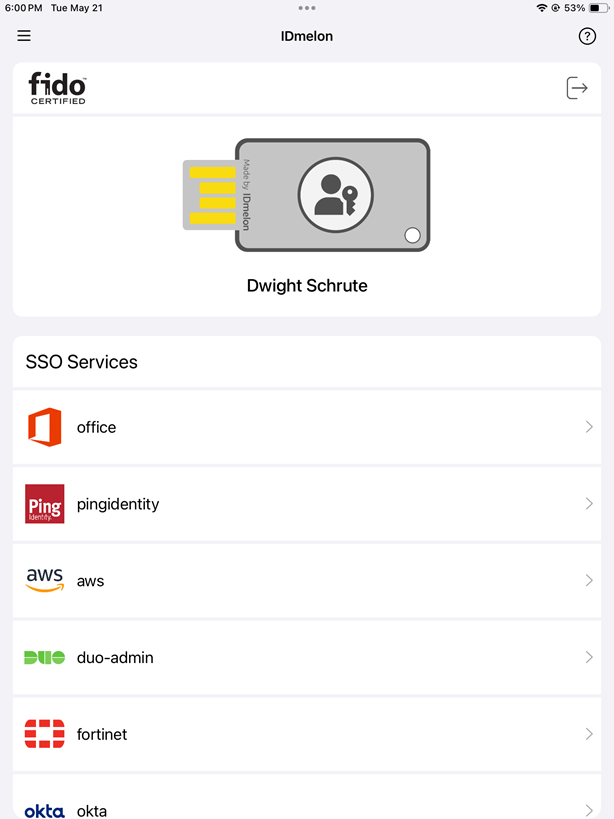
- In case of successful login, user information will be displayed. At this stage, move the app to the background.
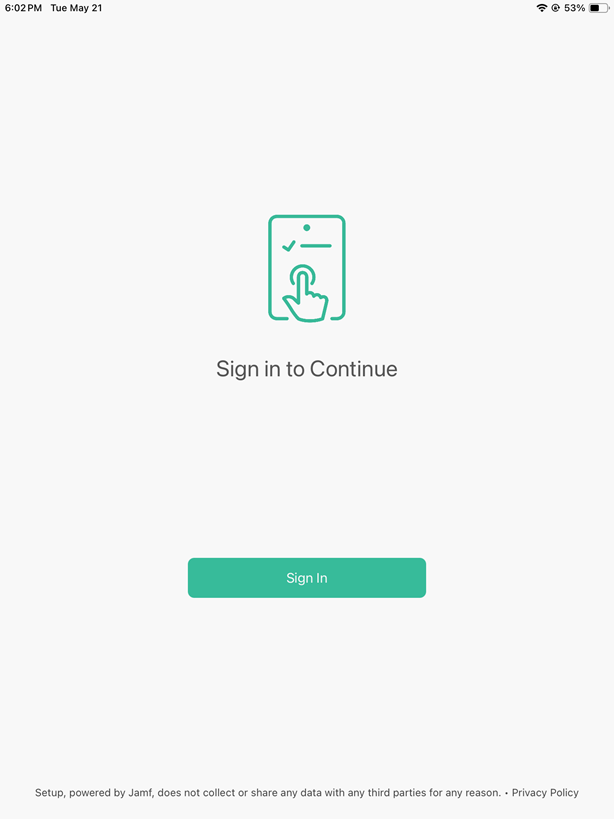
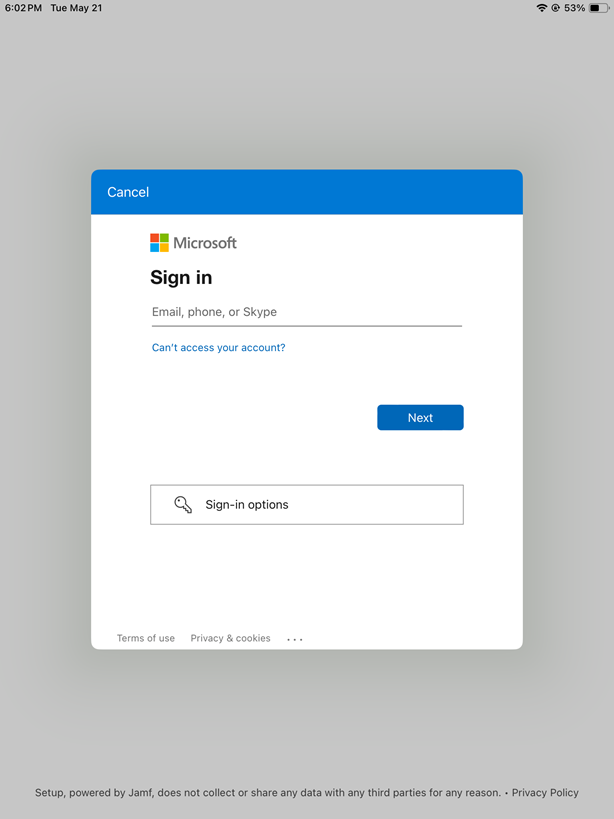
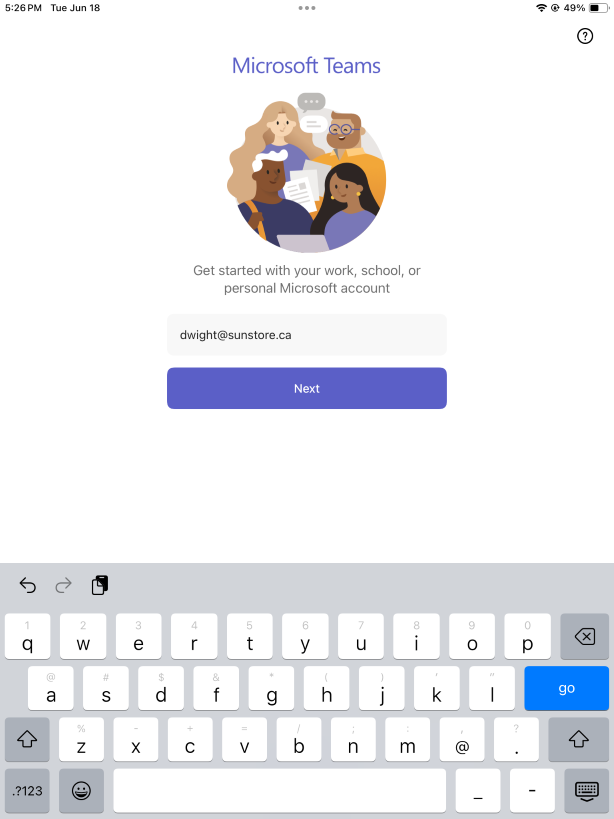
- Open the Jamf Setup app and tap on the Sign In button.
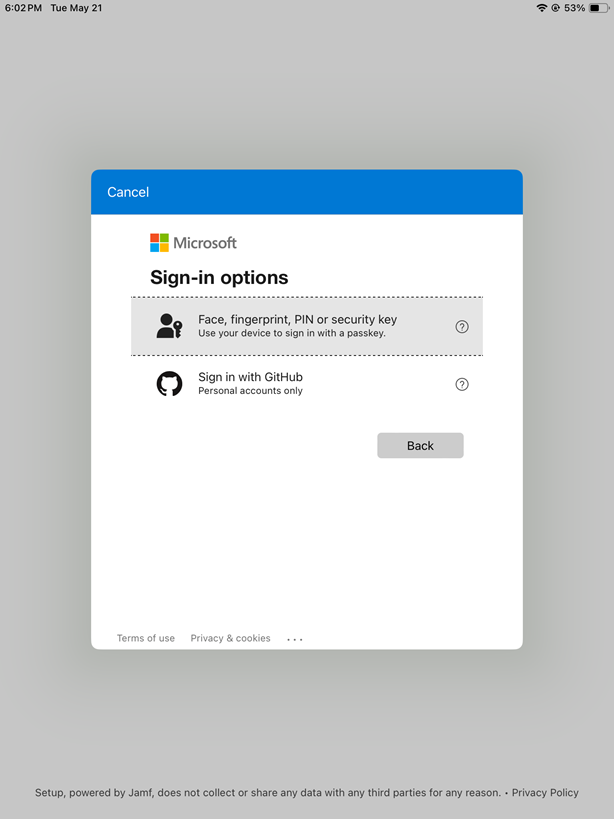
- Select the Sign-in options.
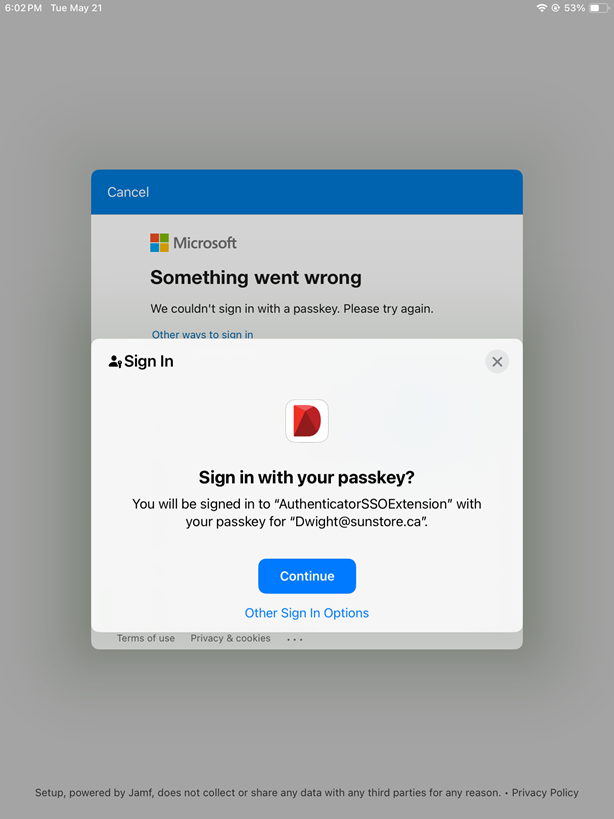
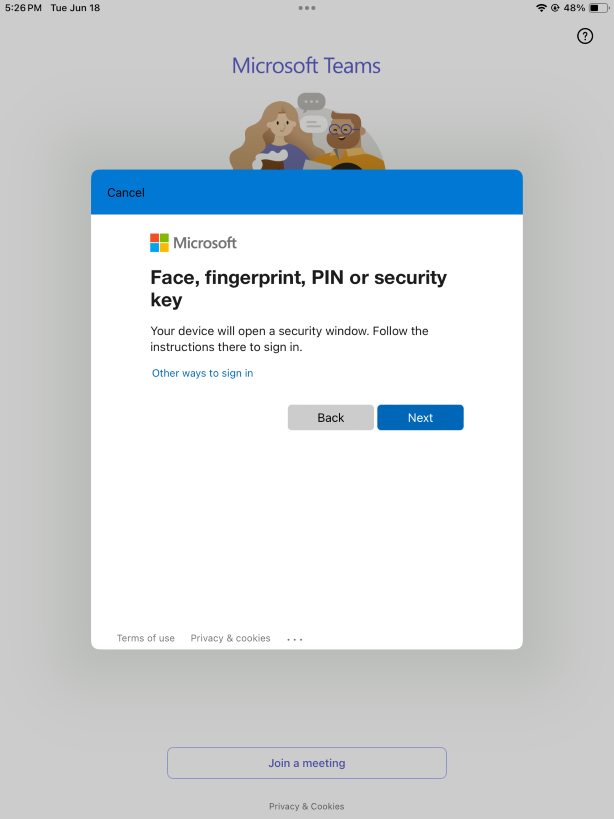
- Select the Face, fingerprint, PIN or security key.
- Tap the Continue.
- If the login operation is successful, you will see the following view, which can be different depending on your configuration in Jamf.
Logout Experience
At the end of the shift, first, open the IDmelon Authenticator and then tap the logout icon on the top right corner of the app. Your user information and existing passkeys will be deleted from the iPad.
If Soft Reset is enabled in Jamf Reset, to completely log out of all your accounts, first open one of the Microsoft applications (for example, MS Teams) and log out of it. After that, all your sessions and cookies will be completely deleted.
Shared Device Mode Configuration Using Intune
Microsoft Intune is a cloud-based endpoint management solution. It manages user access to organizational resources and simplifies app and device management across your many devices, including mobile devices, desktop computers, and virtual endpoints.
Prerequisites
- To use the shared iPad feature, the OS version of iPads must be 17 or later.
How to Configure
- Navigate to Apps > iOS/iPadOS.
- Click the Add button.
- Select iOS store app as the App type and click the Select button.
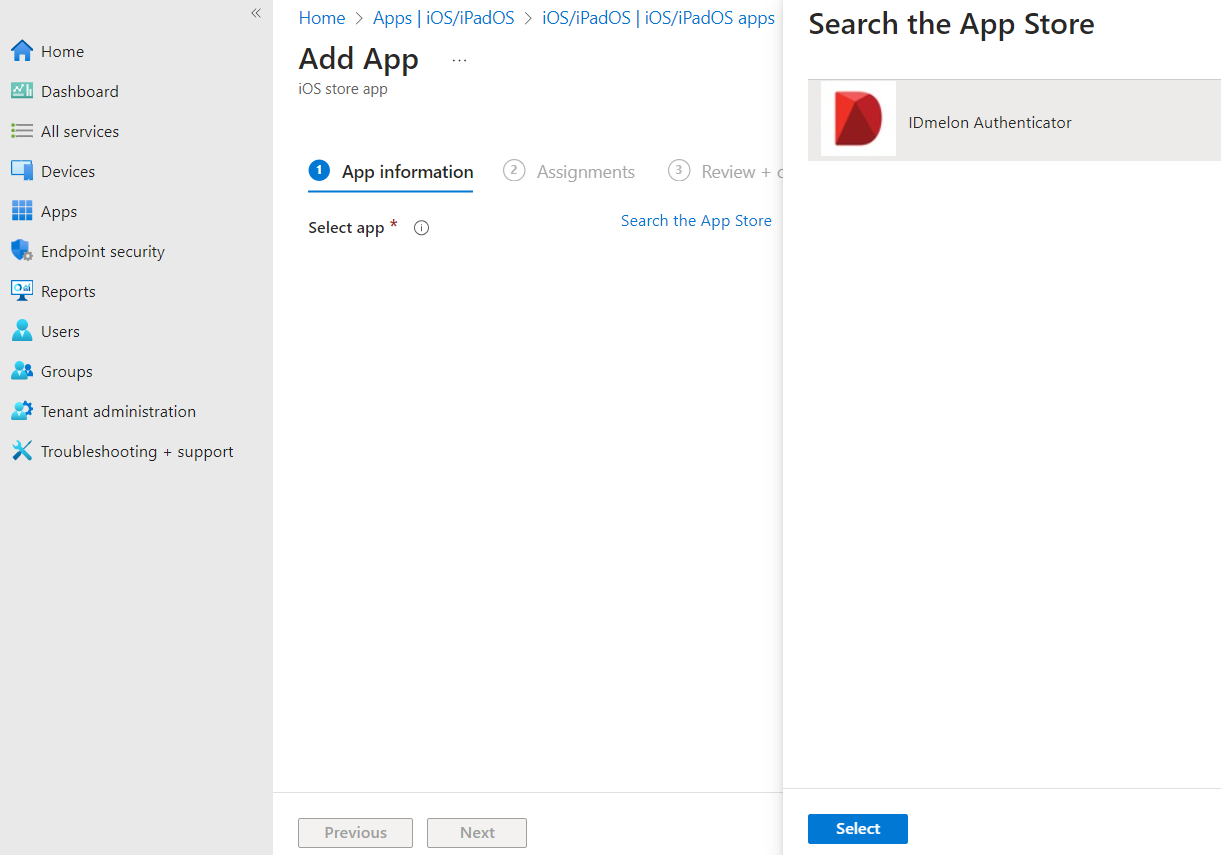
- Click the Search the App Store.
- Search for the IDmelon Authenticator app and click the Select button.
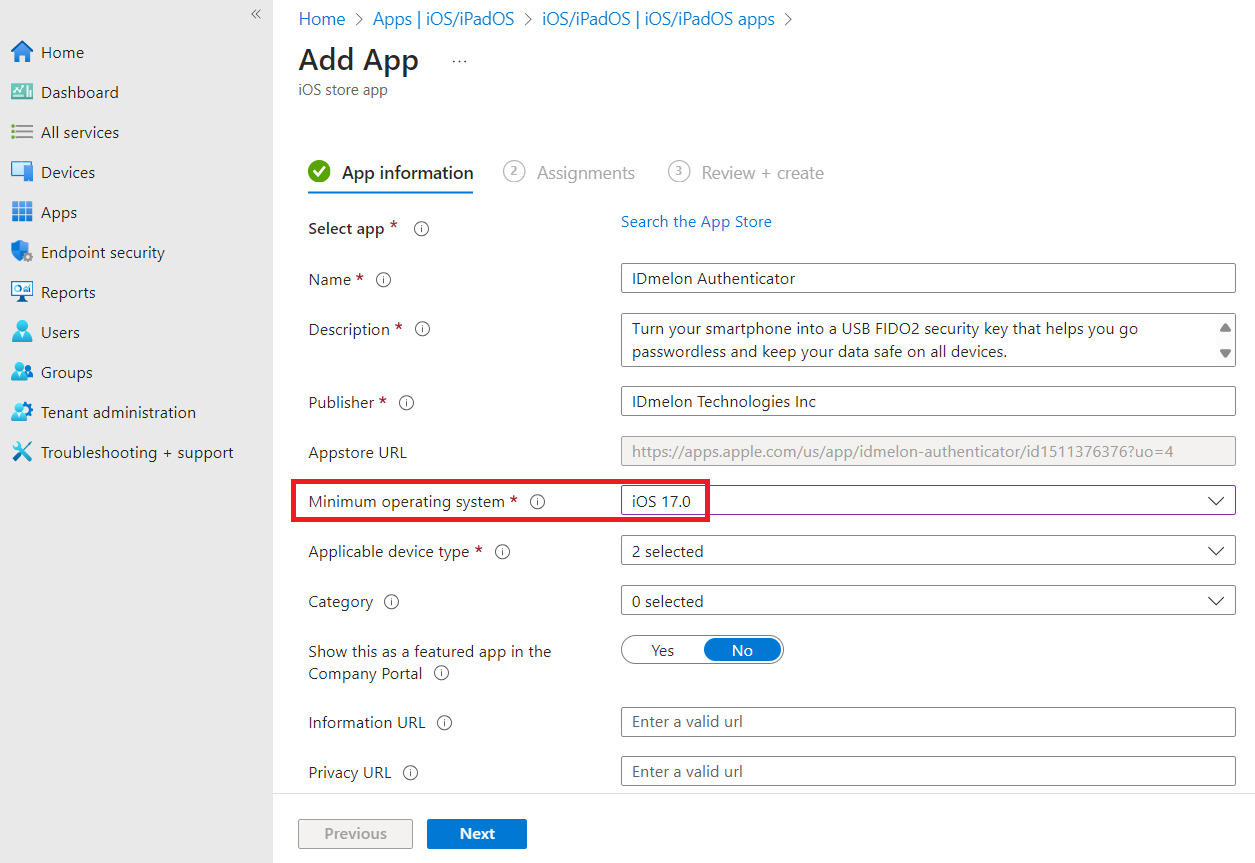
- Select iOS 17.0 as the Minimum operation system and click the Next button.
- Configure the Assignments tab according to your organization’s policies.
- Review the configurations you set and click the Create button.
- Navigate to Apps > App configuration policies, click the + Add, and then Managed devices.
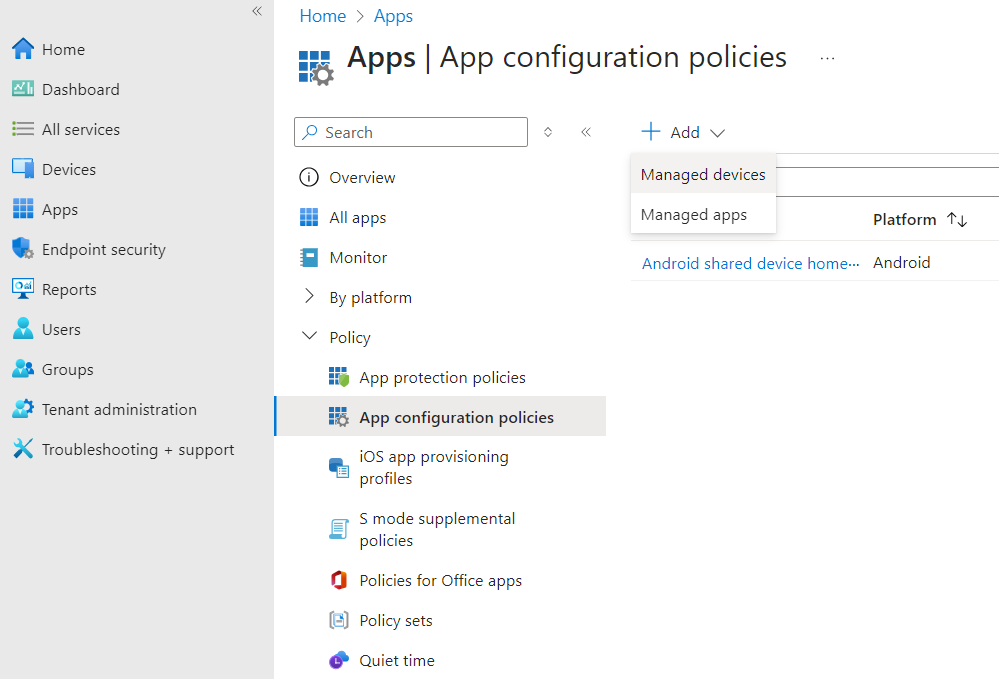
- Set a Name, select the iOS/iPadOS as the Platform, and IDmelon Authenticator as the Targeted app, then click the Next button.
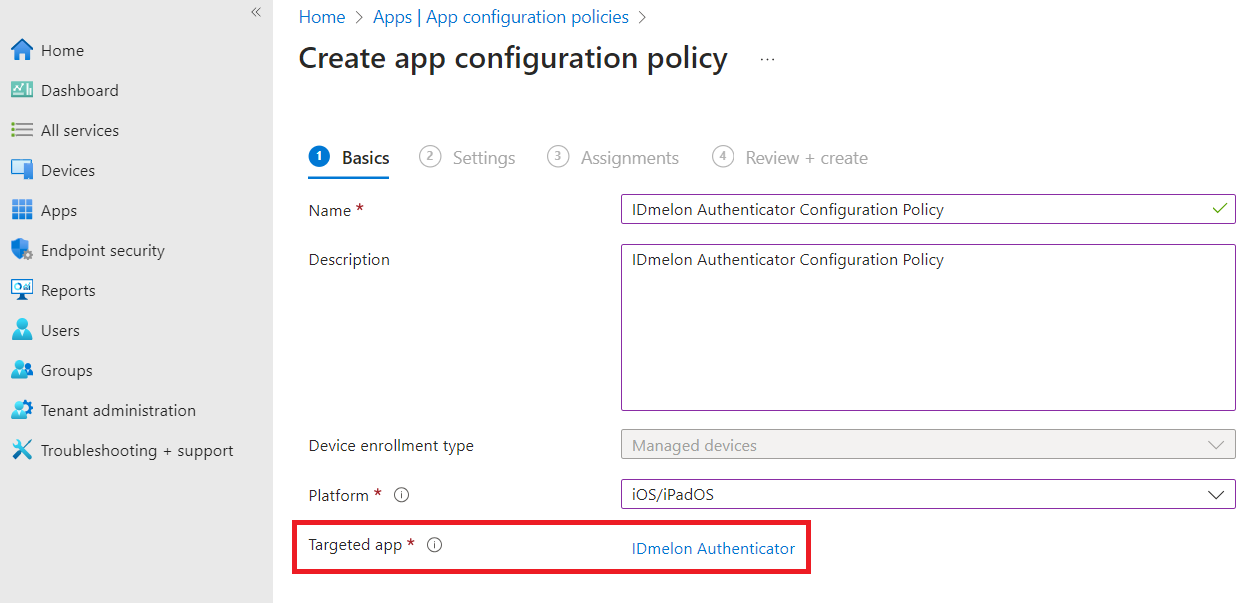
- In the Settings tab, select the User configuration designer as the Configuration settings format, Enter values for the XML property list as below, and click the Next button.
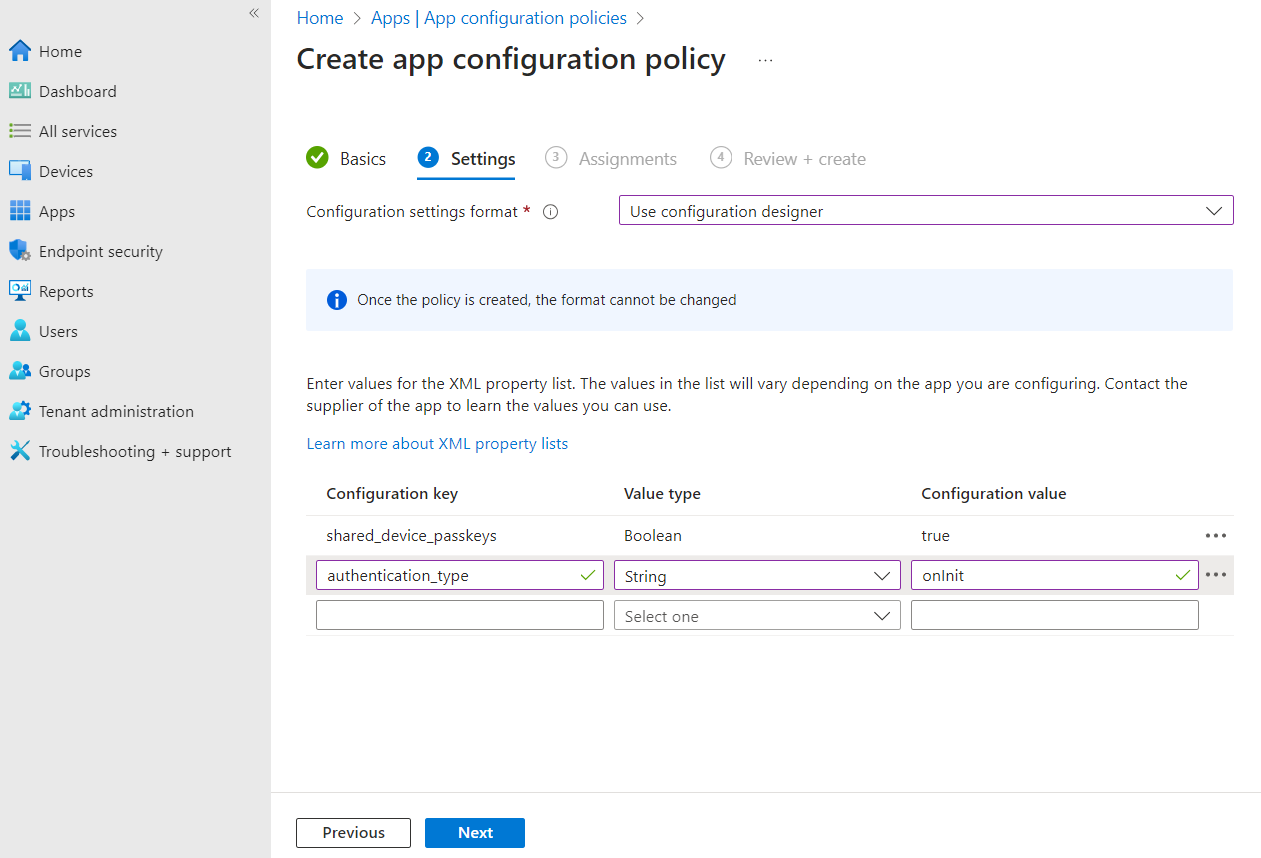
| Configuration key | Value type | Configuration value |
|---|---|---|
| shared_device_passkeys | Boolean | true |
| authentication_type | String | onInit |
| device_id | String | {{deviceid}} |
| api_key | String | [API_KEY] |
One-Time Use Passkeys:
Add the following key to the above configurations to automatically log the user out after their first login with the passkey.
| Configuration key | Value type | Configuration value |
|---|---|---|
| one_time_use_passkeys | Boolean | true |
Dedicated Deployments Base API URL:
If you are using dedicated deployment, such as on-premises, add the following key-value to the configurations.
| Configuration key | Value type | Configuration value |
|---|---|---|
| base_api_url | String | https://example.com/api/url |
Self Service URL:
By adding the self-service URL (available in the IDmelon Admin Panel > Security Keys > Workflows > Self-Service Actions) to the configurations, users will be redirected to the enrollment page if their card is not yet registered.
| Configuration key | Value type | Configuration value |
|---|---|---|
| self_service_url | String | https://panel.idmelon.com/self-service/{UID} |
Auto Logout:
By adding this configuration, users will be automatically logged out of the app after a specified time or after the first use of the passkey.
Allowed values: one-time use, 5m, 60m, 2h, 4h, 6h, 8h
| Configuration key | Value type | Configuration value |
|---|---|---|
| auto_logout | String | 2h |
Generate a New API Key:
The API Key is required to activate IDmellon Authenticator automatically when it is run for the first time. Therefore, there would be no need for manual activation to connect to the organization.
To generate a new API Key, take the following steps:
- Sign in to the IDmelon Admin Panel.
- Navigate to Workspace > Settings > API Key Management.
- Select Create.
- Set a name.
- Set the type to Shared Mobile.
- Copy and replace the generated key with the API_KEY value in the app configuration, which can be found in the table of the 11th step in the previous section.
Allowed values for authentication_type:
- onInit: User is required to enter PIN once only after tapping the card on a reader.
- onUse: User is required to enter PIN for each login.
- none: The login process is done without entering any PIN (PINless mode).
12. Configure the Assignments tab according to your organization’s policies, and click the Next button.
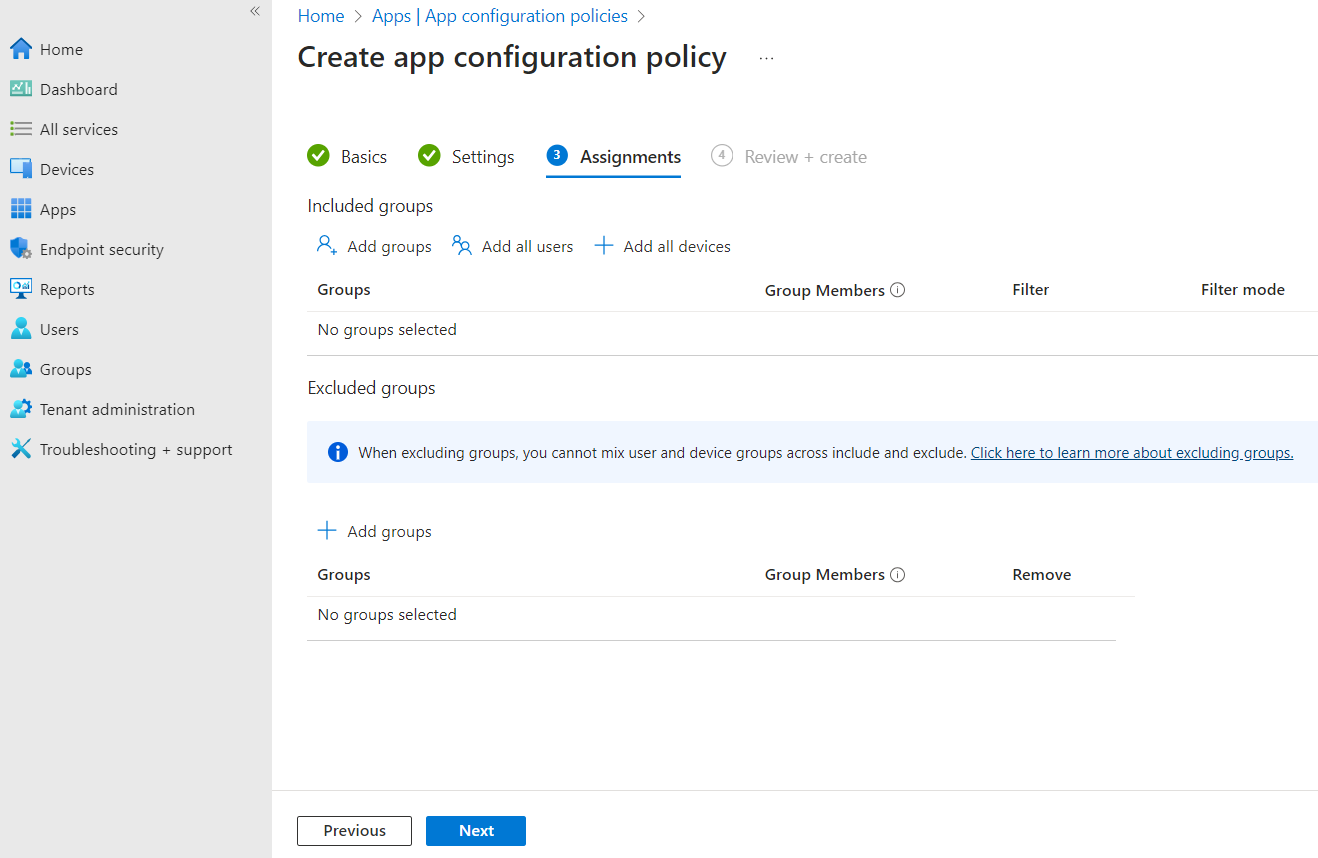 13. Review the configurations you set and click the Create button.
13. Review the configurations you set and click the Create button.
Connect to the Organization:
To set up the IDmelon Authenticator as the organization’s shared device, Follow the steps similar to the link below.
End User Experience
The login steps are as follows: at the beginning of the shift, an employee will first log in with their card, and at the end of the shift, by exiting the application, everything will be ready for the next person.
Note: If you use Microsoft applications (MS Teams, PowerBI, etc …), the Microsoft Authenticator app must be added and configured as shared device mode.
Config MS Authenticator as shared device mode
- Open the IDmelon Authenticator.
- Get close to the reader and tap your card on it.
- According to the Card Verification Method set in the IDmelon admin panel, if PIN is required, enter it. Otherwise, go to the next step.
- In case of successful login, user information will be displayed. At this stage, move the app to the background.
- Open the app you want to log in with the passkey (e.g. MS Teams), tap the paste icon on the top left corner of the keyboard, and tap the Next.
- Tap the Next.
- Tap the Continue.
Logout Experience
- Open the app you logged into, and log out of the account.
- Open the IDmelon Authenticator and then tap the logout icon on the top right corner of the app. Your user information and existing passkeys will be deleted from the iPad.
Shared Device Mode Configuration From the App Settings
To manually adjust some of the shared iPad’s configs, do it from the following path:
App Menu > Security Key Settings > App Configs.
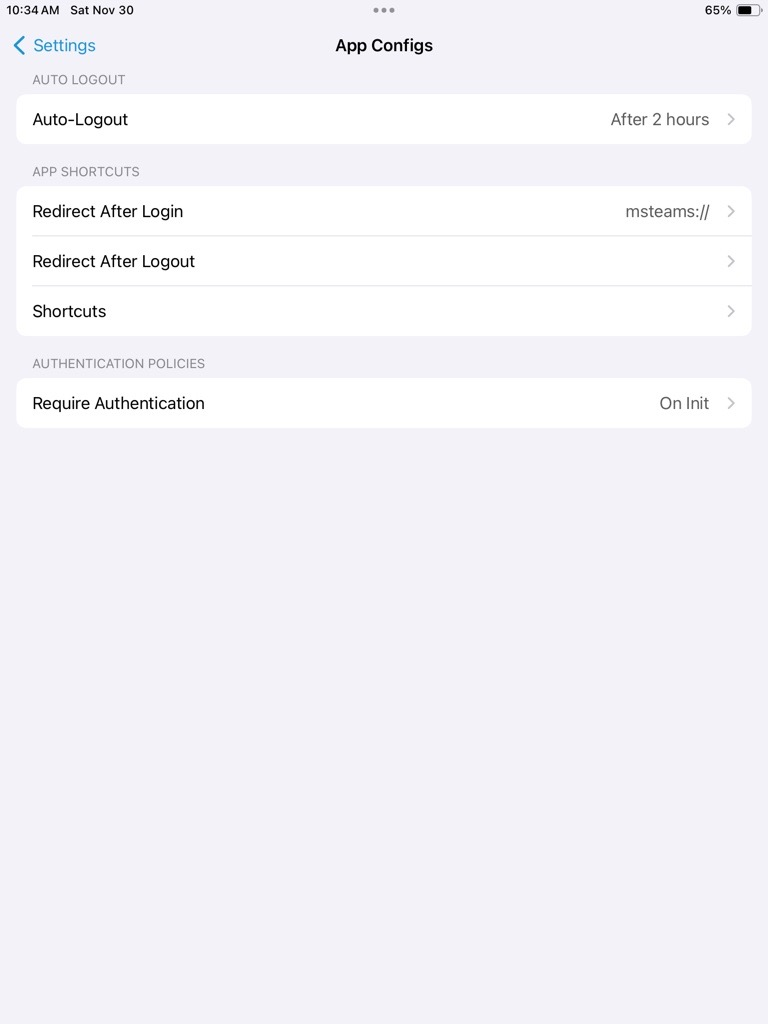
Auto-Logout:
By enabling this config, users will be automatically logged out of the app after a specified time or after the first use of the passkey.
Redirect After Login:
By enabling this config, users will be redirected to a specific app or URL after logging in. (e.g., msteams:// will open the Microsoft Teams app if it is available on the device).
Redirect After Logout:
Similar to “Redirect After Login,” after users log out, they will be redirected to the desired app or address.
Require Authentication:
- On Init: Users must enter a PIN once after tapping the card on the reader.
- On Use: Users are required to enter a PIN for each login.
- None: The login process is completed without entering any PIN (PINless mode).
Note: The value of the Require Authentication depends on the Card Verification Method that your organization’s admins have set in the IDmelon admin panel.