Active Directory Federation Service (AD-FS)
In this document you are going to set up AD-FS as an external IdP to the IDmelon.
Initialize IDmelon Configuration as SP
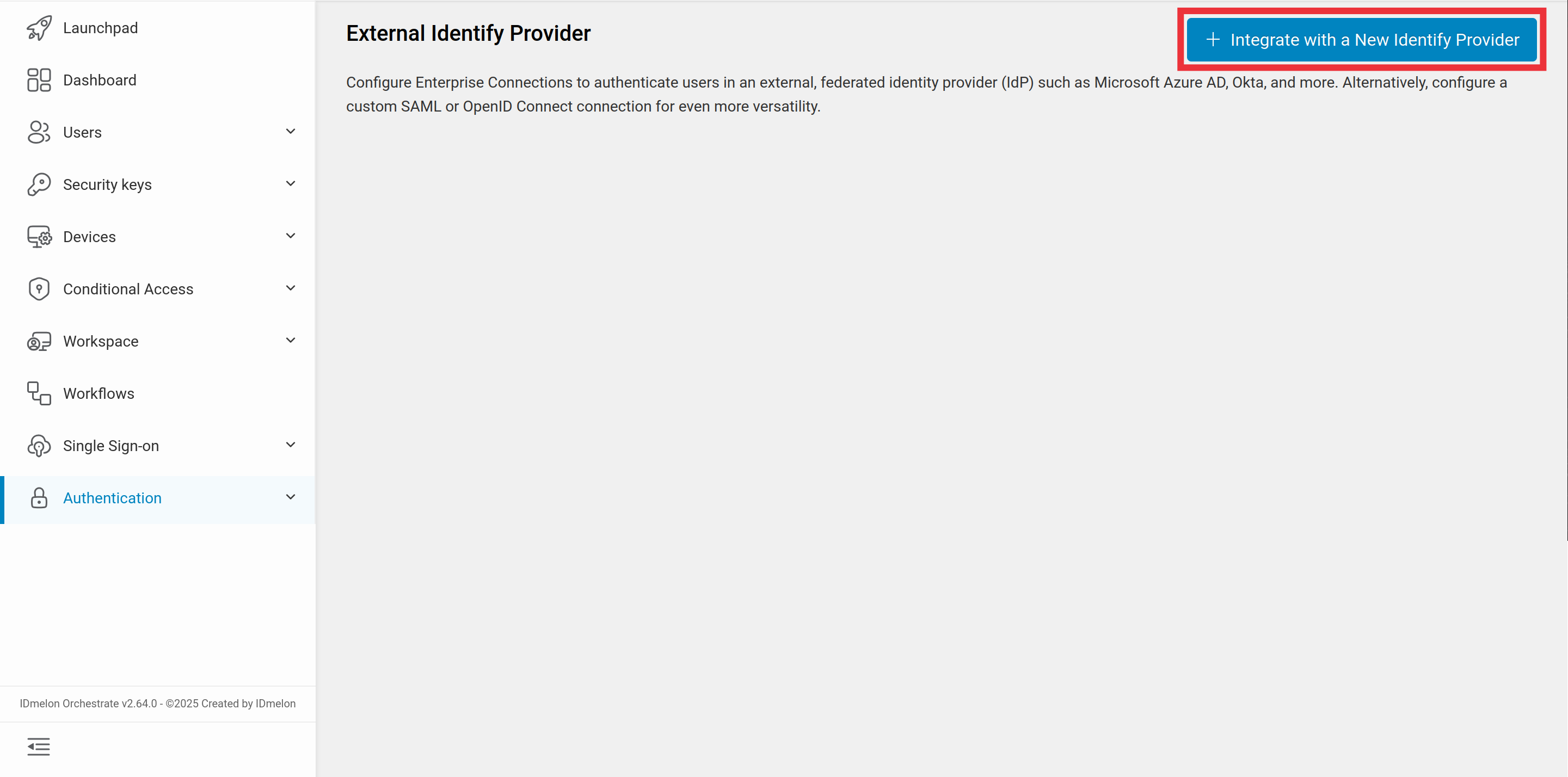
Log in to the IDmelon panel, navigate to the Authentication section, and click Integrate with a New Identity Provider:
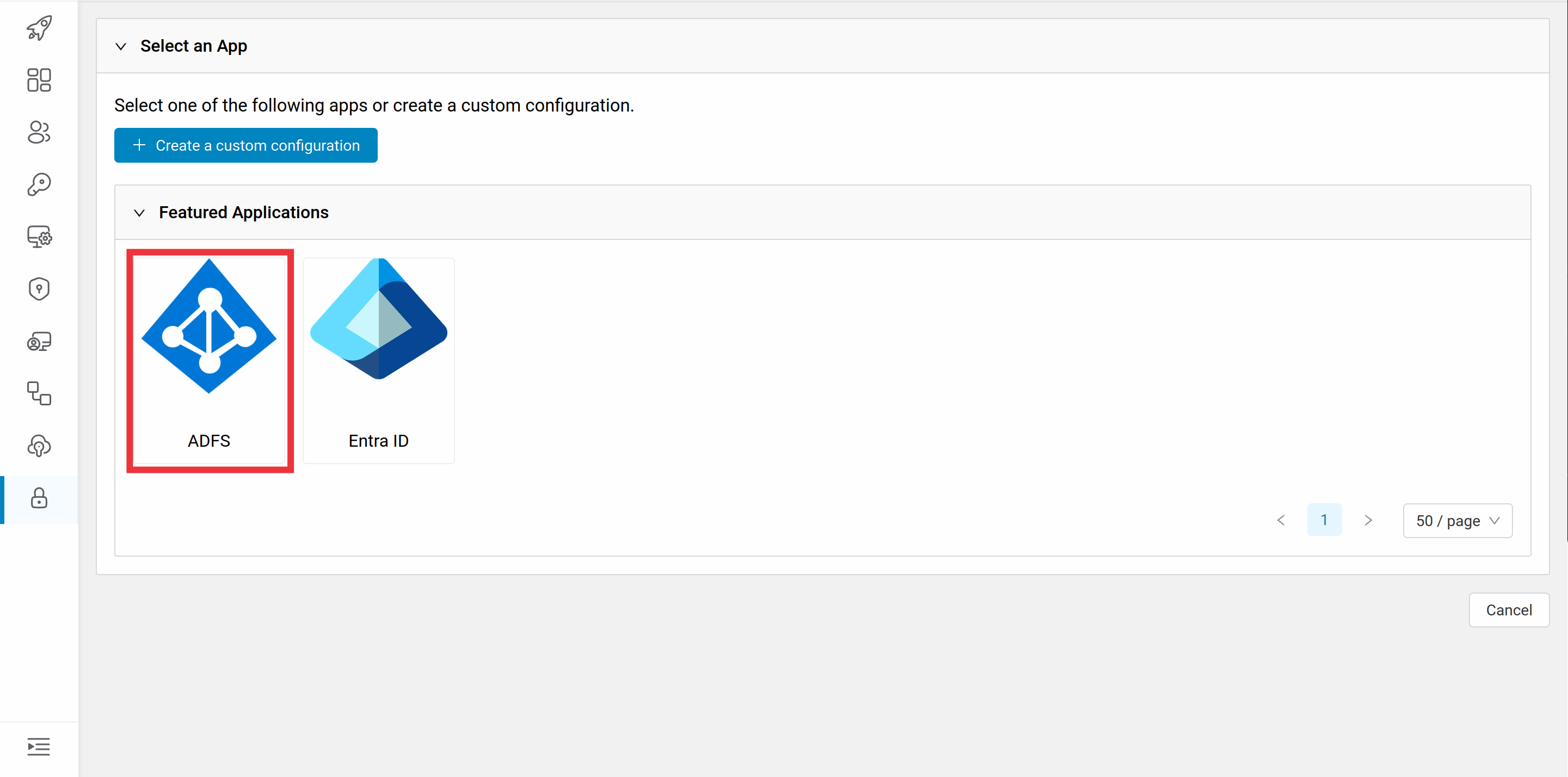
Then select ADFS as identity provider:
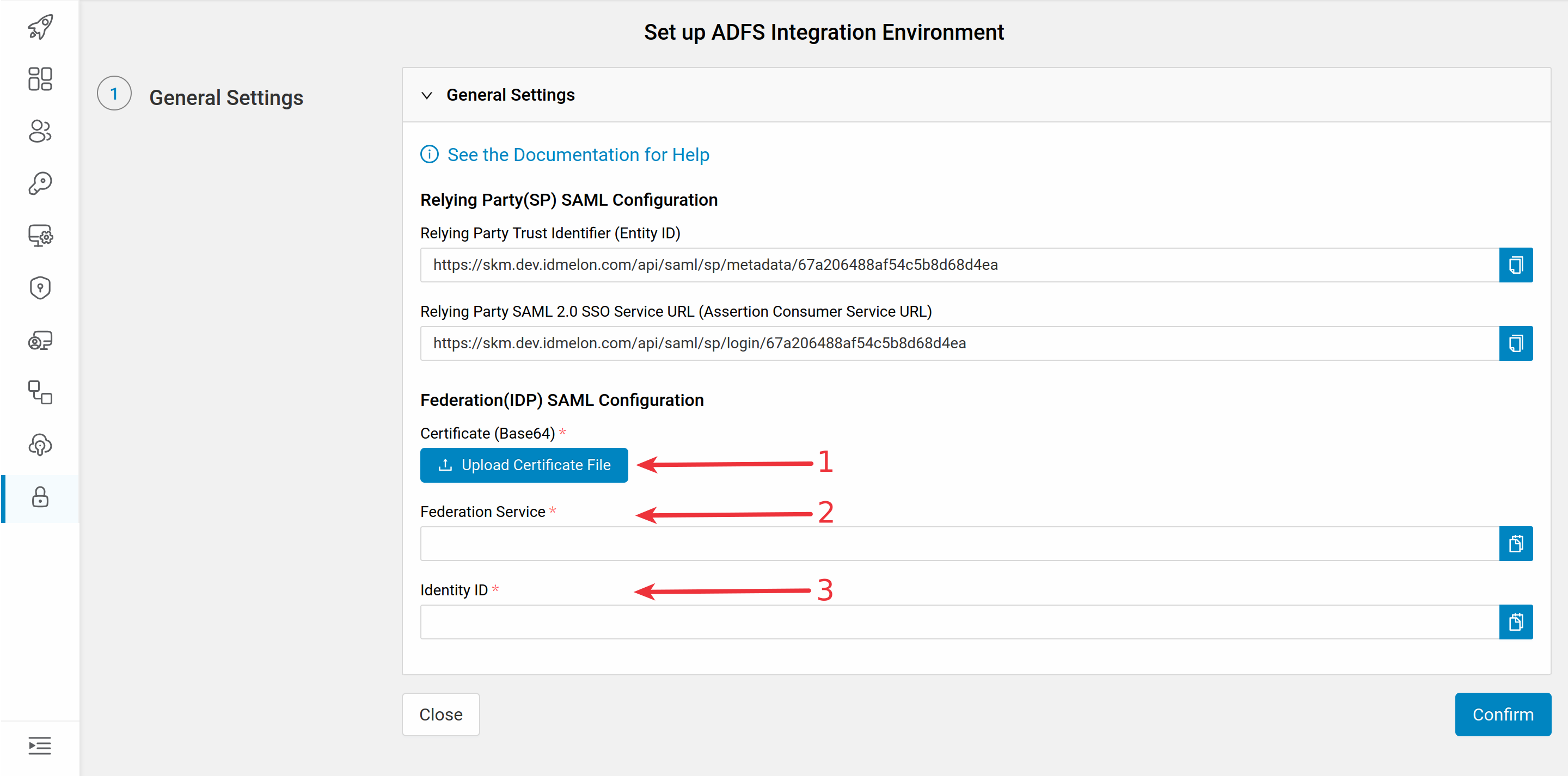
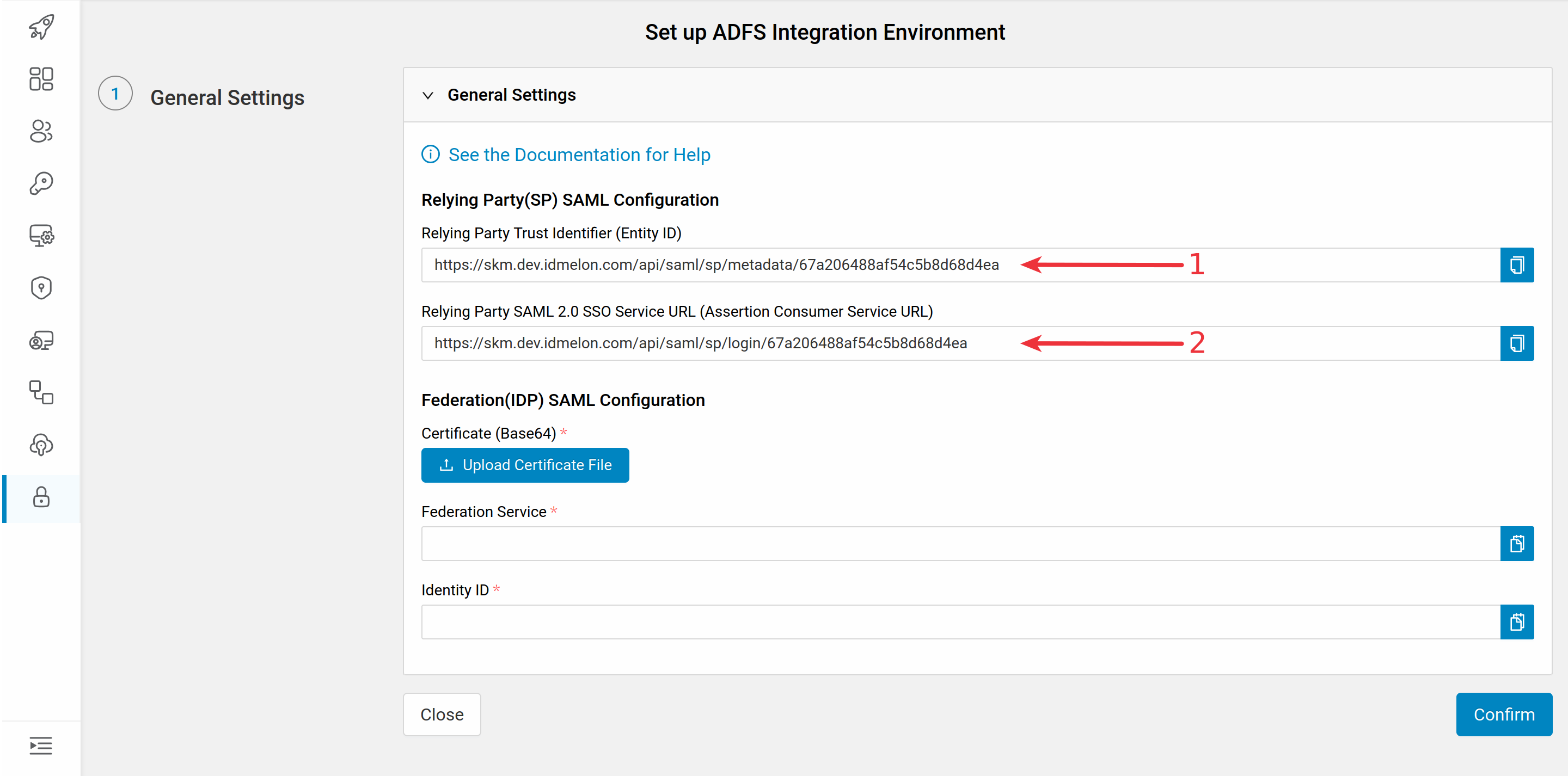
You will need the values provided in the newly opened window to set up ADFS as an external IDP:
Configuring AD-FS as external IDP
Navigate to Server Manager > Tools > AD FS Management > right click on Relying Party Trust > Add Relying Party Trust
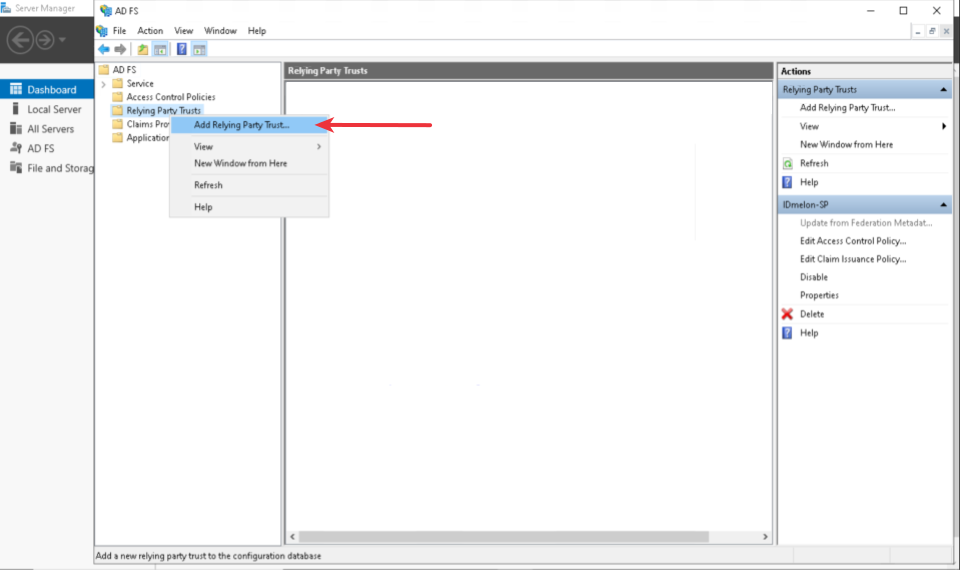
Select the Claims Aware option
Click on start.
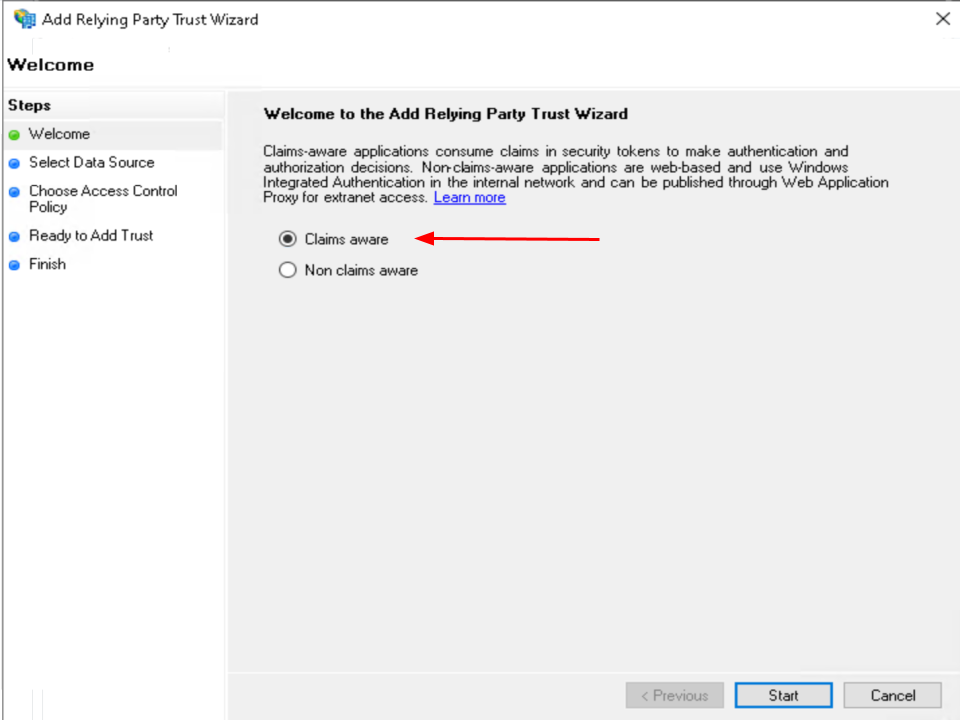
Select the Enter data about the relying party manually option
Click on Next.
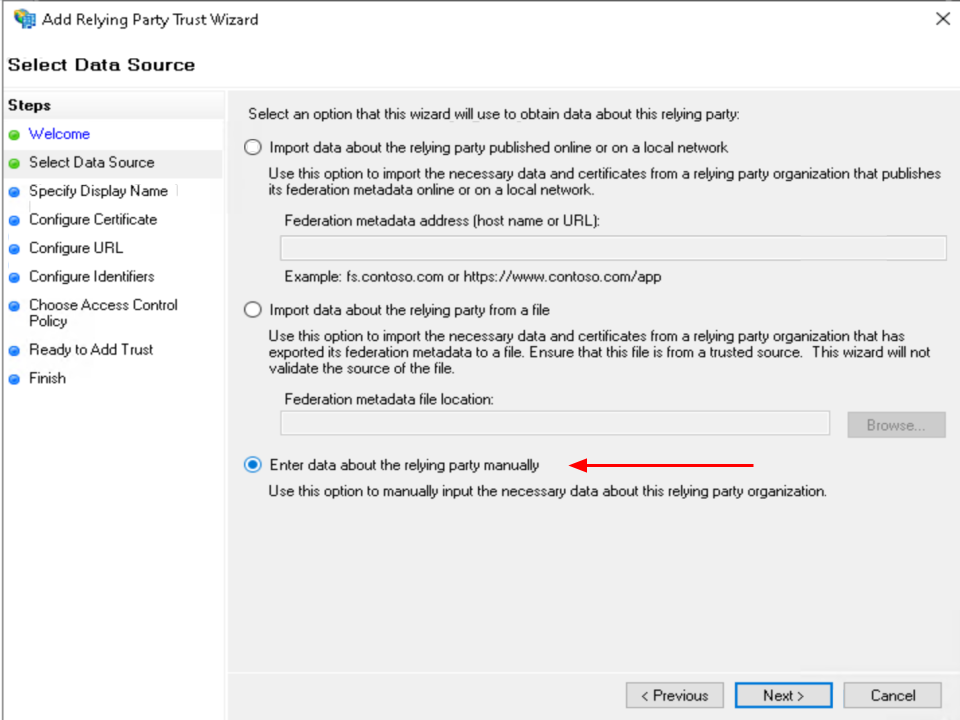
Select the Enter data about the relying party manually option
Click on Next.
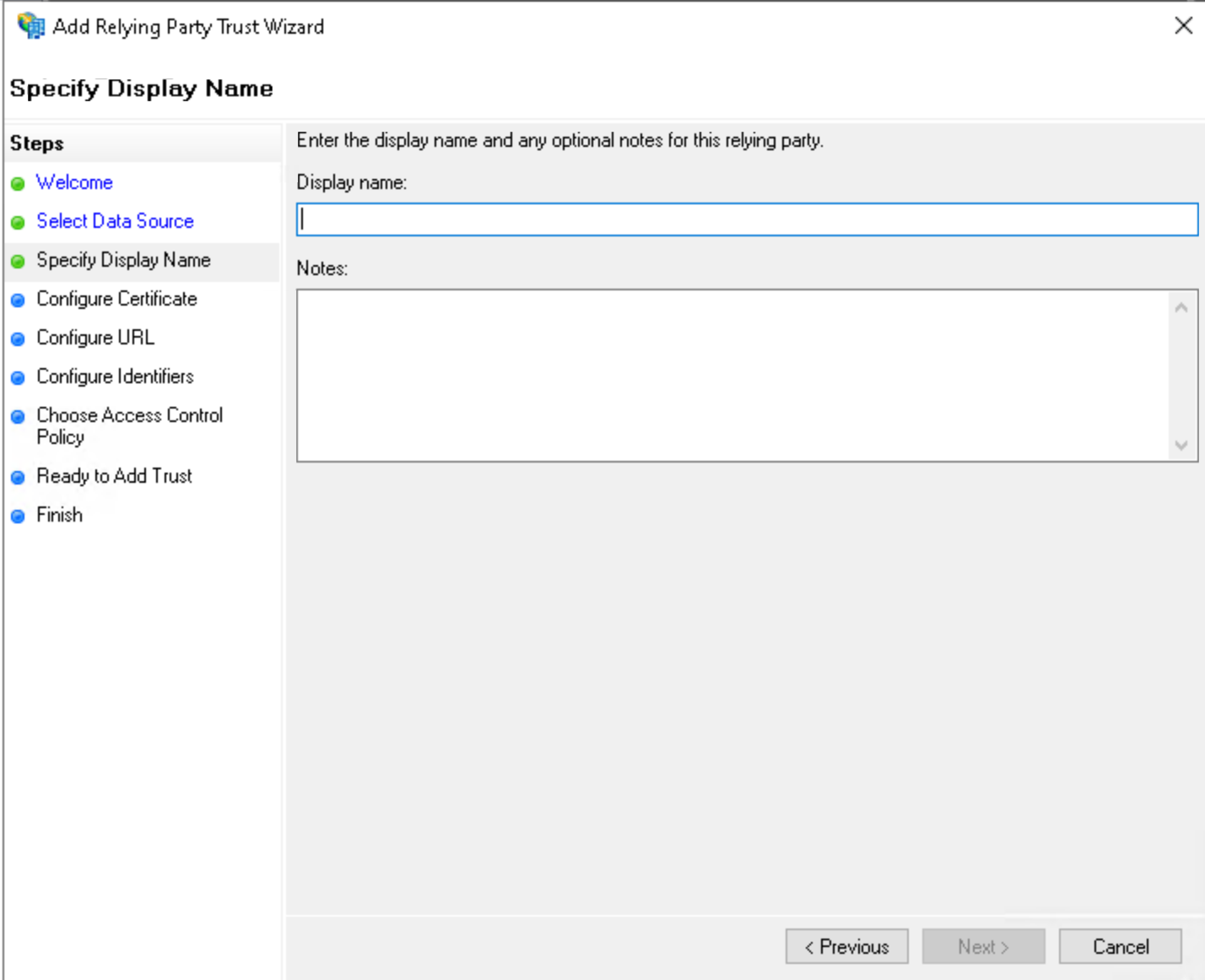
Provide a Display name
Add a Description
Click on Next.
- Click on next (No Changes).
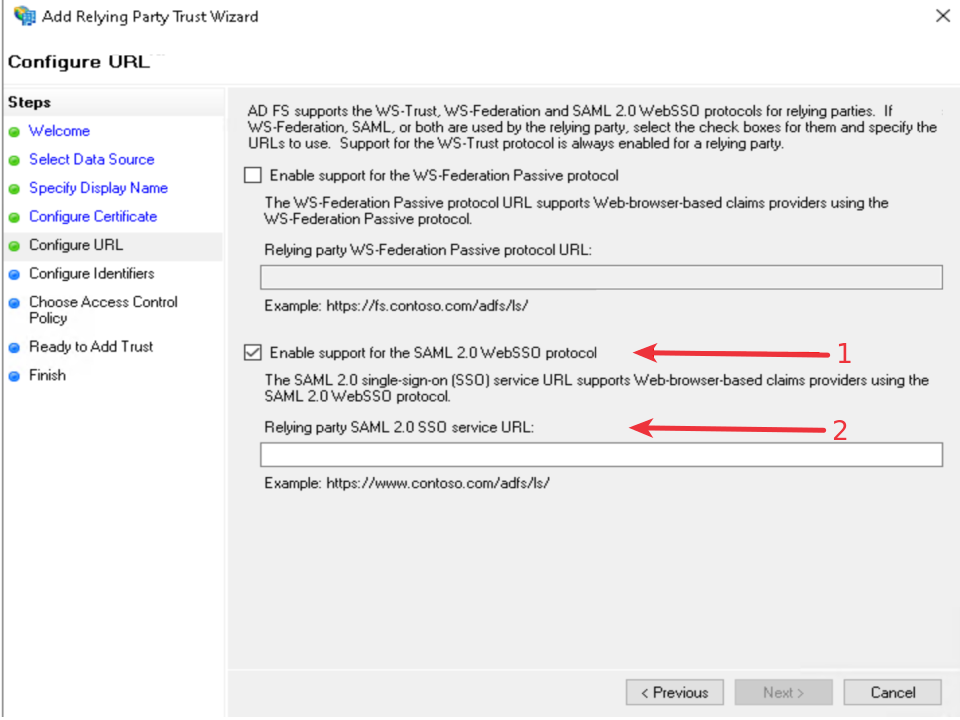
Select the Enable support for the SAML 2.0 WebSSO protocol option
Provide Relying party service URL from IDmelon panel
Click on Next.
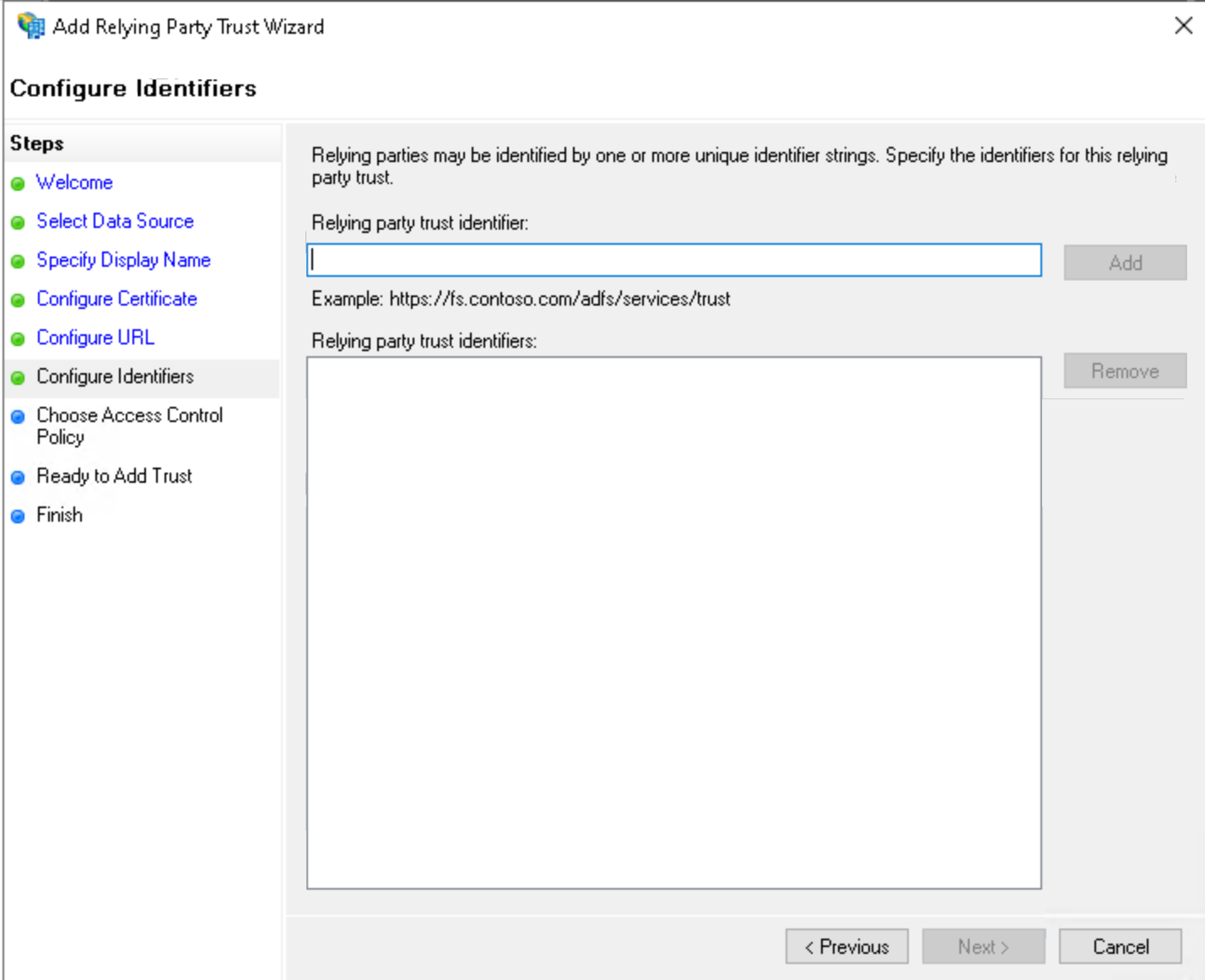
Provide Relying party trust identifier from IDmelon panel
Click on Add.
Click on Next.
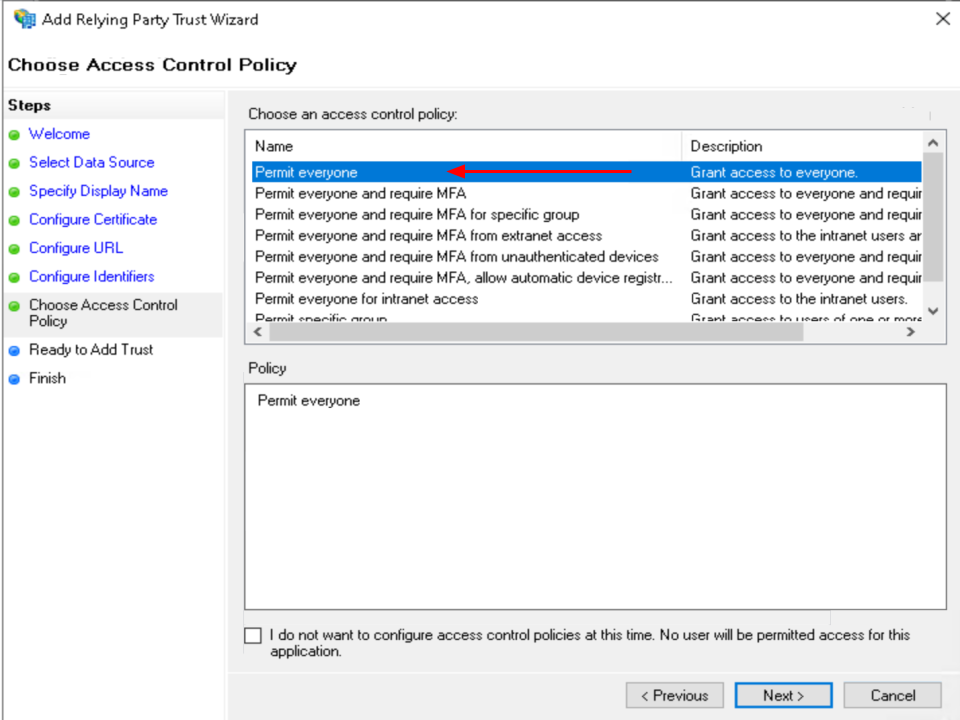
Select Permit everyone option
Click on Next.
- Click on Next (No Changes).
- Click on Close (No Changes).
Configuring Claims (Attribute Mappings)
- Select your newly created federation configuration, then choose
Edit Claim Issuance Policyfrom the right-hand menu.
- Click on Add Rule.
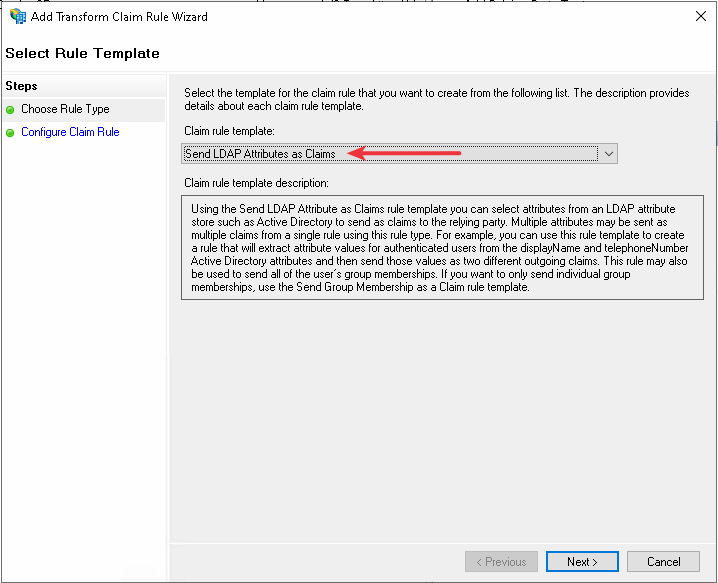
Select Send LDAP Attributes as Claims option
Click on Next
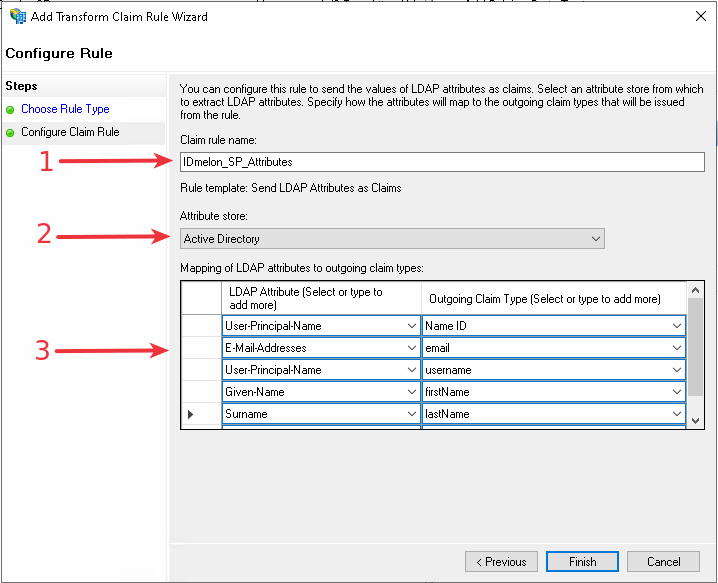
Provide a name
Select Active directory option
Select Claims options as follows:
- User Principle Name =>
Name ID - E-MailAddress =>
email - Given Name =>
firstName - Surname =>
lastName - User Principle Name =>
username
- User Principle Name =>
Click on Finish
Finishing IDmelon Configuration as SP
On the AD FS server, open PowerShell and run the following command to retrieve the server name:(Get-AdfsProperties).Hostname
Return to the IDmelon Authentication Panel and complete the required fields as shown in the images.
- AD-FS certificate
- https://<ADFS_SERVER_NAME>/adfs/ls/
- http://<ADFS_SERVER_NAME>/adfs/services/trust