CyberArk
⚠️ Important Notice
The content in this document is currently under review and will be updated soon. We are actively working on providing you with the most accurate and up-to-date information. Thank you for your patience and understanding.
In this document you are going to set up IDmelon as an external IdP to the CyberArk.
Login to CyberArk administration panel
In order to set up the connection, you will need to log into your CyberArk administration panel.
Add Identity Provider
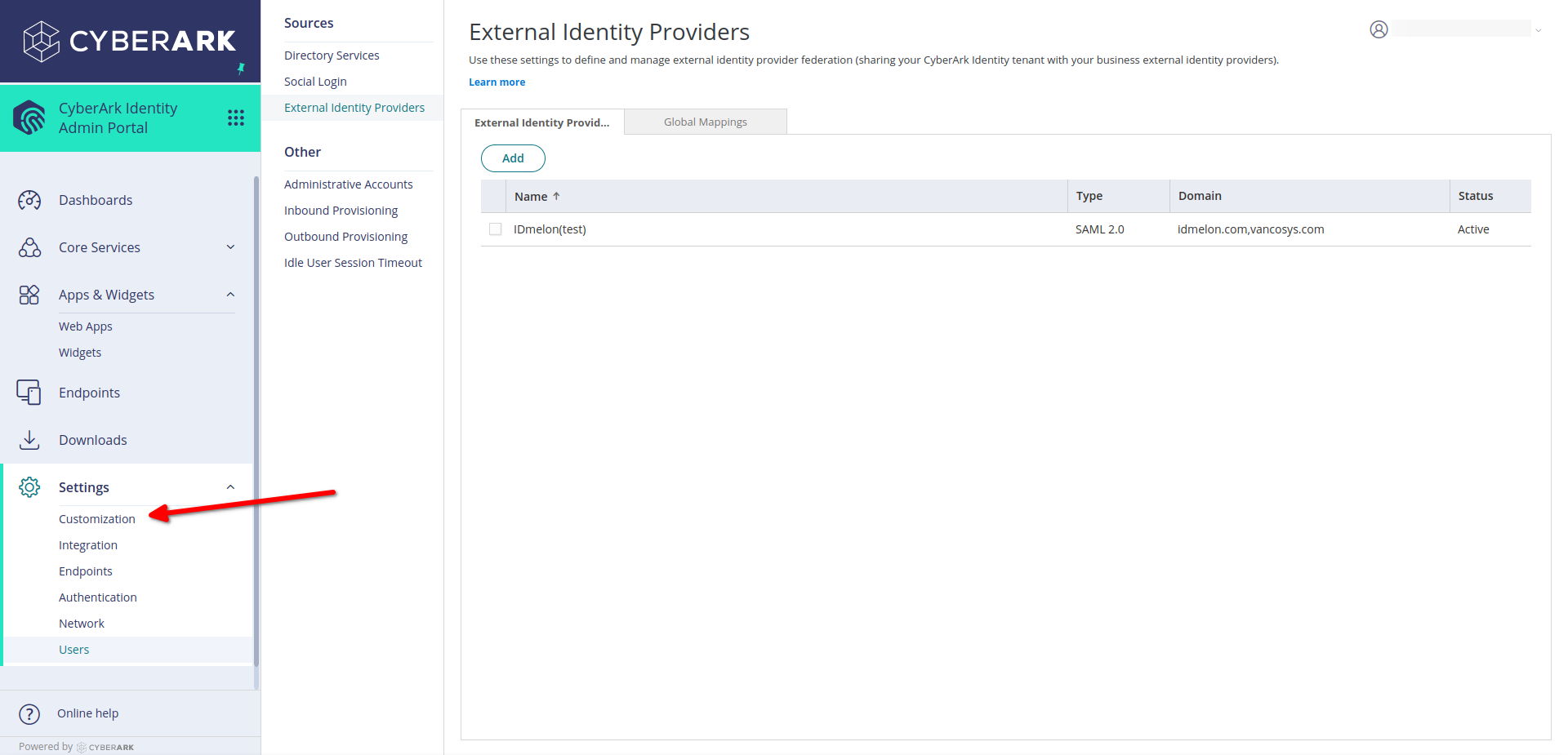
In the CyberArk administration panel, from the side menu, navigate to the Settings menu, then click Users.
Under the Sources, click External Identity Providers.
Click Add to add a new IdP config.
In the External Identity Providers Name, choose your custom IdP name.
- External Identity Providers Name:
Your custom name
Activate the Active button to redirect your users to IDmelon.
- Active:
Click to Active
Choose SAML 2.0 as Federation Type.
- Federation Type:
SAML 2.0
For Federation Domains, add your custom users' domain as many as your users have.
- Federation Domains:
Your custom user domains
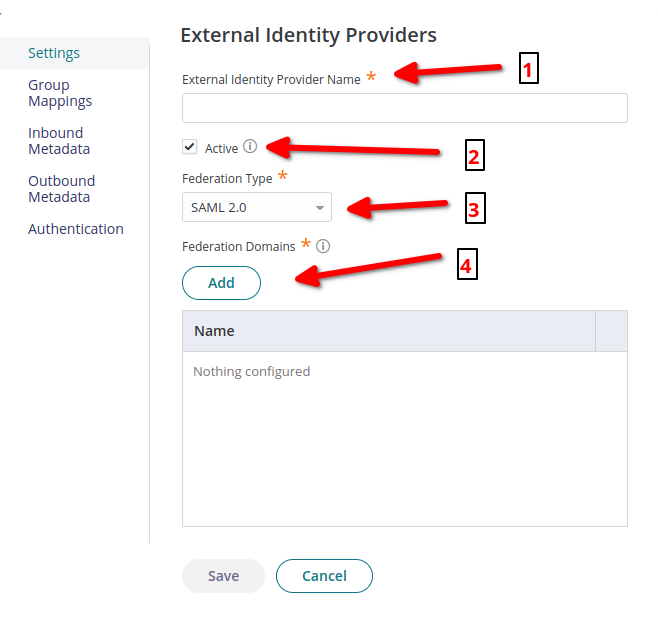
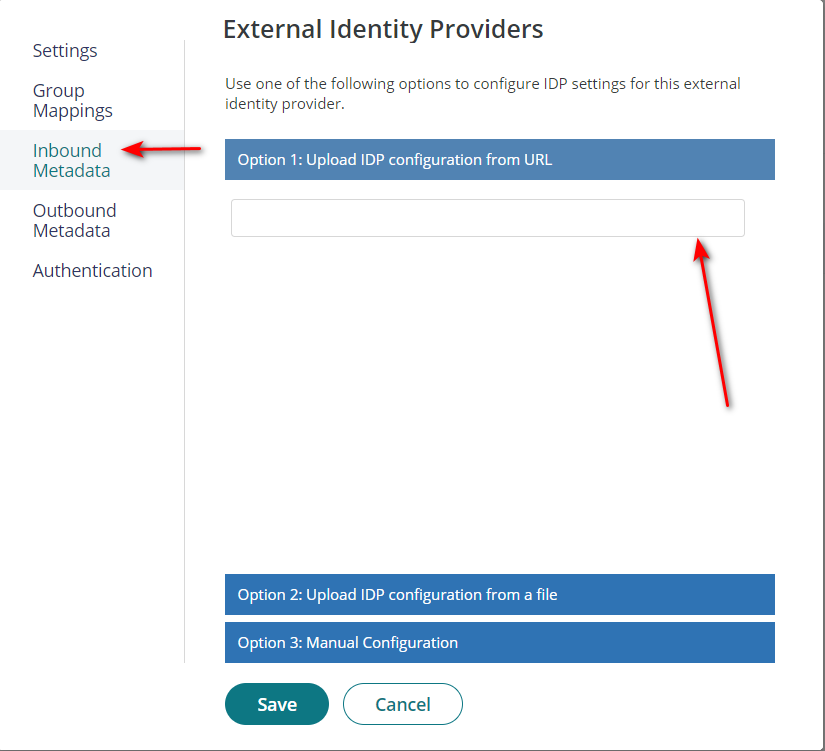
Then click Inbound Metadata option.
There are several options which IDmelon supports, but IDmelon recommends to Upload IdP configuration from URL.
Get all values for
{..}from your IDmelon panel. If you are currently logged in here, you will see the replaced values instead.
- Upload IdP configuration from URL: idp_issuer_uri
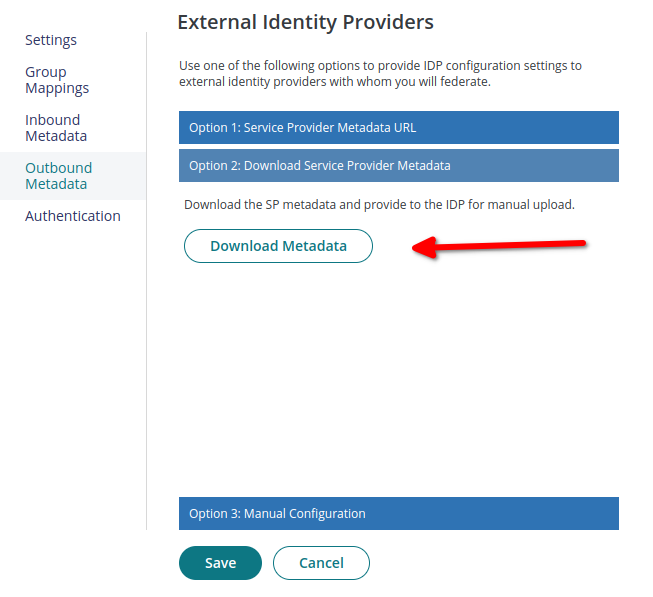
Then click **Outbound Metadata option.
IDmelon SAML configuration
You should download metadata file and copy values of below fields from this CyberArk panel to IDmelon
Panel.
- Download Service Provider Metadata: Download Metadata
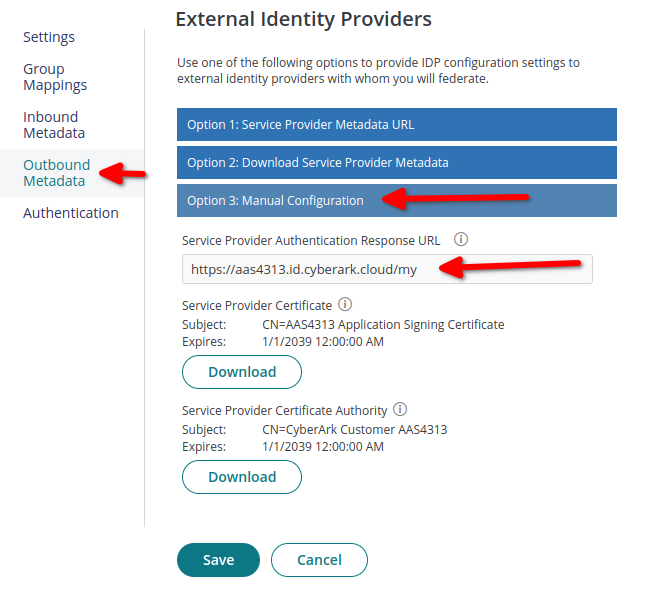
Click on Manual Configuration.
Assertion consumer service : Copy Service Provider Authentication Response URL.
Entity id : CN=CyberArk:Customer:{your custom subdomain in capital words}
My company Domain is https://aas4313.id.cyberark.cloud/ so my company subdomain which CyberArk provided will be :
abl4313 so my entity id will be Example : CN=CyberArk:Customer:ABlL4313 .
- You should copy values of below fields from this CyberArk panel to IDmelon Panel.
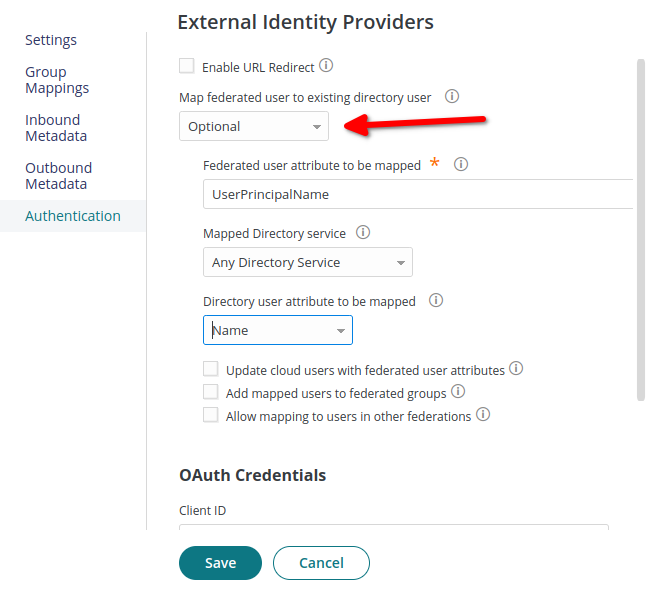
Then click **Authentication option**.
In order to map IDmelon and CyberArk users, choose Optional in the Map federated user to existing directory use.
- Map federated user to existing directory use:
Optional
- Click Save.
Tips
- Optional: Selecting
Optionalmeans authentication of a mapped federation user results in the user of the mapped directory service. If a user cannot be mapped, a new federated user is created. - Required: Selecting
Requiredmeans the user of a federation will authenticate as the matching user of another directory service. If no match is found, login is denied. IfCreate cloud user if unable to mapis also enabled, a matched CyberArk Cloud Directory user is created and login is permitted.
Suffixes for users domain Tips
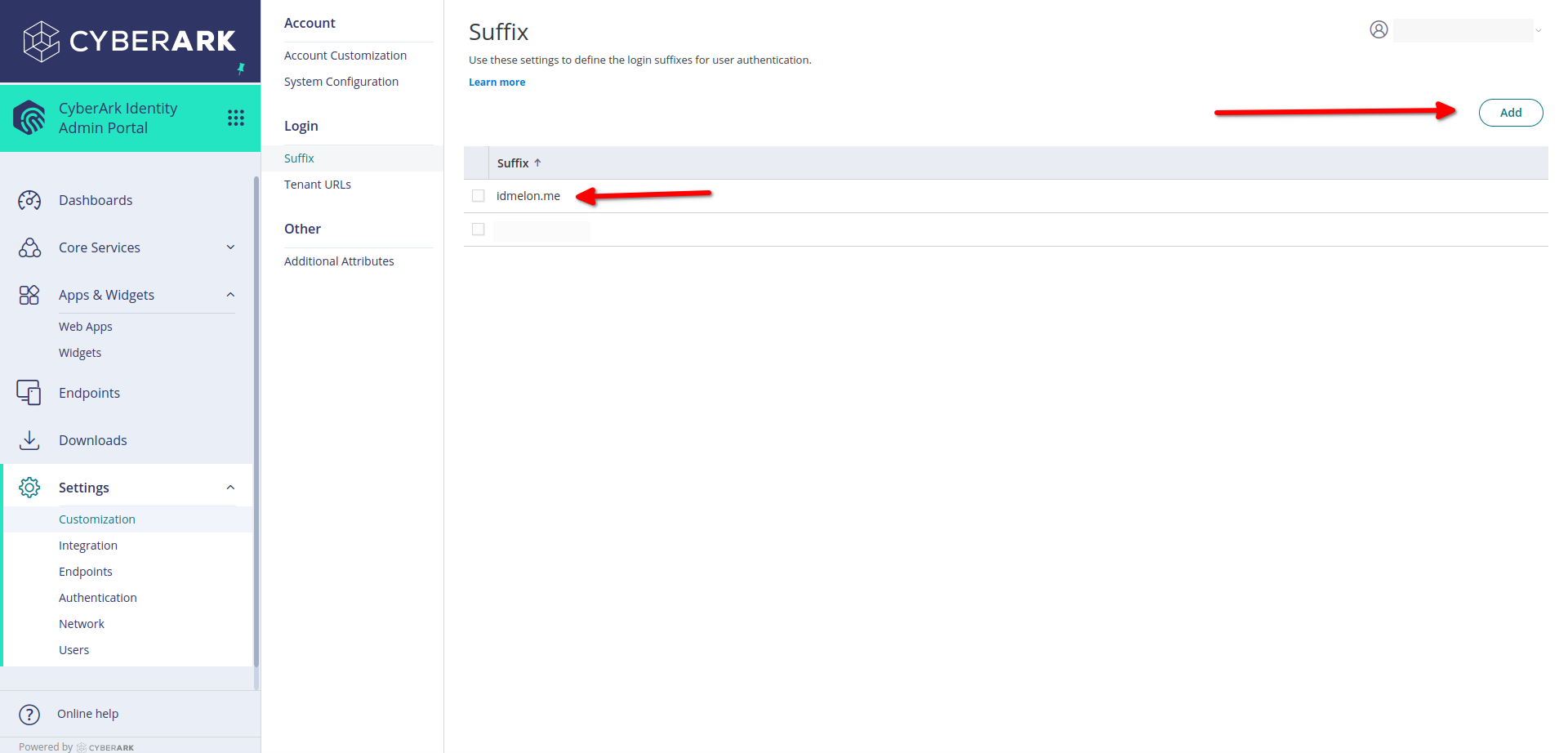
In the CyberArk administration panel, from the side menu, navigate to the Settings menu, then click Customization.
Then under the Login, choose Suffix, Click on Add button which is on the Right hand of the dashboard.
Add Custom Login Suffix, example: username@idmelon.com
- Login Suffix:
username@Your custom domain
On the Advanced option, users can be mapped and log in with another suffix.
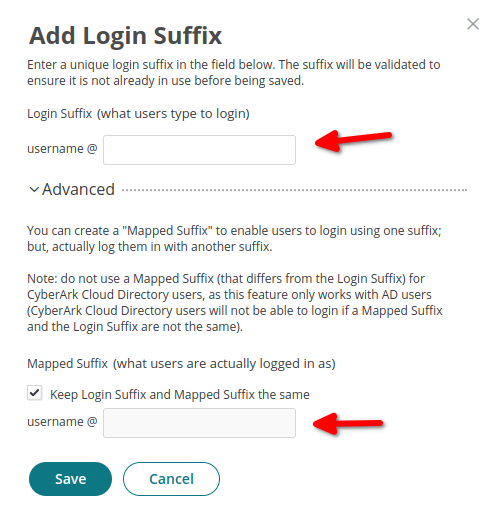
map users for sso: If you want to use another suffix domain which does not exist in CyberArk but the user information exists in IDmelon, you have to uncheck
Keep Login Suffix and Mapped Suffix the sameand chooseyour custom user domain, Example : [email protected]Click Save.